It is comprised of an attribute, such as the username or password, and a value for that particular attribute. This privacy statement applies solely to information collected by this web site. Use the tacacs-server host command to specify the IP address of one or more TACACS+ daemons: tacacs-server host hostname [single-connection] [port integer] [timeout integer] [key string] Step 3. It occurs when a client passes the appropriate credentials to a security server for validation. Users can always make an informed choice as to whether they should proceed with certain services offered by Adobe Press. Each hash has the previous hash linked into its input values, and the end result is referred to as the pseudo pad. WebRADIUS uses the UDP protocol while TACACS+ uses the TCP protocol. how many times was the civic arena roof opened. eou Set authentication lists for EAPoUDP. While these analytical services collect and report information on an anonymous basis, they may use cookies to gather web trend information. The NAS can either follow this response or view it as a FAIL. As we learned earlier in this chapter, Accounting is configured via the aaa accounting global configuration command. For example, if the query is presented in character mode (e.g. session-duration Set the preference for calculating session durations. We communicate with users on a regular basis to provide requested services and in regard to issues relating to their account we reply via email or phone in accordance with the users' wishes when a user submits their information through our Contact Us form. This group will contain servers with IP addresses 10.1.1.1, 10.1.1.2, and 10.1.1.3. In addition to this, Authorization can be applied to terminal lines (e.g. The first example illustrates how to configure Authorization for PPP (network) using the method list PPP-AUTHOR. Now that we have a solid understanding of the configuration requirements for AAA servers and server groups, we will move on to the configuration of AAA services, beginning with Authentication. Instead, it relies on a combination of a hashing function and an XOR or EOR algorithm, which is an algorithm that basically means either one or the other, but not both. The request is accepted and the configure terminal command is successfully authorized on R1, as illustrated in step 4. load-balance Server group load-balancing options. As with the previous two records, this record also includes information that was included in the Authorization process and other specific information pertaining to the user account. We may revise this Privacy Notice through an updated posting. Save up to 70% on N10-008 exam prep and validate your skills. Pearson collects information requested in the survey questions and uses the information to evaluate, support, maintain and improve products, services or sites; develop new products and services; conduct educational research; and for other purposes specified in the survey. Pearson may disclose personal information, as follows: This web site contains links to other sites. Pearson may provide personal information to a third party service provider on a restricted basis to provide marketing solely on behalf of Pearson or an affiliate or customer for whom Pearson is a service provider. TACACS+ also implements authentication, authorization, and accounting separately, which makes it possible for each functionality to be delegated to a different server, and/or even a different type of server (non-TACACS+). WebTACACS+ is a Terminal Access Controller Access Control System is a protocol that is suitable for the communication between the Cisco server and the client. Pearson collects name, contact information and other information specified on the entry form for the contest or drawing to conduct the contest or drawing. dot1x Set authentication lists for IEEE 802.1x.  And Accounting is used to allow for an audit trail, i.e. These tickets have a limited lifespan and are stored in a users credential cache. Having stated that, we will now move on to the second part of the AAA framework: Authorization. If TACACS+ authorization is required, the TACACS+ server is again contacted and it returns an ACCEPT or REJECT authorization response. WebIn what settings is it most likely to be found?
And Accounting is used to allow for an audit trail, i.e. These tickets have a limited lifespan and are stored in a users credential cache. Having stated that, we will now move on to the second part of the AAA framework: Authorization. If TACACS+ authorization is required, the TACACS+ server is again contacted and it returns an ACCEPT or REJECT authorization response. WebIn what settings is it most likely to be found?  IPCP for PPP, IP addresses(s) for the tunnel endpoint, e.g. Your email address will not be published. This TACACS+ server group will contain servers with IP addresses 10.1.1.254, 172.31.1.254, and 192.168.1.254. It allows organizations to create a private network by utilizing the public network. Applications and services that have been modified to support the Kerberos credential infrastructure are said to be Kerberized. This keyword is used to enable Authorization for Console access. User, device, and services information can be replicated between multiple servers, which provide redundancy in large networks. VPN bypasses network congestion from untrusted sources. These tickets can then be used in place of the standard username/password Authentication scheme. The following diagram provides a basic illustration of TACACS+ Authorization communication: In the diagram illustrated above, the remote user (who has been successfully authenticated), issues the show run command on the NAS (R1), as illustrated in step 1. Console and VTY) as required by the administrator. The name is found and the TACACS+ server sends a request for a password (REPLY), as illustrated in step 6. Disabling or blocking certain cookies may limit the functionality of this site. Each record includes an AV pair for Accounting and one of three types may be sent: STOP (indicates when a service is about to stop, or when a service is stopped), CONTINUE (is sent when a service is still in progress). However, it is recommended that the UDP port number be set to 1813. Multiple security servers can be implemented allowing access control to be added easily. Articles
IPCP for PPP, IP addresses(s) for the tunnel endpoint, e.g. Your email address will not be published. This TACACS+ server group will contain servers with IP addresses 10.1.1.254, 172.31.1.254, and 192.168.1.254. It allows organizations to create a private network by utilizing the public network. Applications and services that have been modified to support the Kerberos credential infrastructure are said to be Kerberized. This keyword is used to enable Authorization for Console access. User, device, and services information can be replicated between multiple servers, which provide redundancy in large networks. VPN bypasses network congestion from untrusted sources. These tickets can then be used in place of the standard username/password Authentication scheme. The following diagram provides a basic illustration of TACACS+ Authorization communication: In the diagram illustrated above, the remote user (who has been successfully authenticated), issues the show run command on the NAS (R1), as illustrated in step 1. Console and VTY) as required by the administrator. The name is found and the TACACS+ server sends a request for a password (REPLY), as illustrated in step 6. Disabling or blocking certain cookies may limit the functionality of this site. Each record includes an AV pair for Accounting and one of three types may be sent: STOP (indicates when a service is about to stop, or when a service is stopped), CONTINUE (is sent when a service is still in progress). However, it is recommended that the UDP port number be set to 1813. Multiple security servers can be implemented allowing access control to be added easily. Articles
 This keyword is used to enable Authorization for beginning an EXEC shell on the selected lines. WebAdvantages/Strengths of VPN-. Before we get into the specifics of RADIUS and TACACS+, let's define the different parts of AAA solutions. Method lists allow control of one or more security protocols and security servers to be used to offer fault tolerance and backup of Authentication databases. In addition to this, TACACS+ separates the three AAA architectures, unlike RADIUS, which groups Authentication and Authorization together and separates Accounting. Pearson Education, Inc., 221 River Street, Hoboken, New Jersey 07030, (Pearson) presents this site to provide information about Pearson IT Certification products and services that can be purchased through this site. View the full answer. TACACS+ While DIAMETER will work in the same basic manner as RADIUS (i.e.
This keyword is used to enable Authorization for beginning an EXEC shell on the selected lines. WebAdvantages/Strengths of VPN-. Before we get into the specifics of RADIUS and TACACS+, let's define the different parts of AAA solutions. Method lists allow control of one or more security protocols and security servers to be used to offer fault tolerance and backup of Authentication databases. In addition to this, TACACS+ separates the three AAA architectures, unlike RADIUS, which groups Authentication and Authorization together and separates Accounting. Pearson Education, Inc., 221 River Street, Hoboken, New Jersey 07030, (Pearson) presents this site to provide information about Pearson IT Certification products and services that can be purchased through this site. View the full answer. TACACS+ While DIAMETER will work in the same basic manner as RADIUS (i.e. 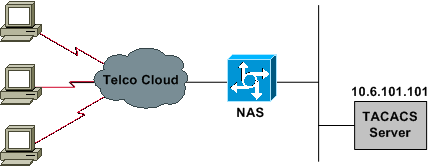 This random value remains the same during the course of the session. Username and password credentials can be stored on the local database of the device and referenced by the AAA services. Authentication must be configured and the AAA client must have successfully authenticated. What is TACACS+ Terminal Access Controller Access Control System (TACACS+) is Cisco proprietary protocol which is used for the communication of the The RADIUS servers will be configured to use ports 1812 and 1813 for AAA services. logins), you must then specify the method list that will be used for Authentication. However, if the username is found in the database and the password is validated, the server returns an Access-Accept response back to the client, as illustrated in step 5. The information gathered may enable Pearson (but not the third party web trend services) to link information with application and system log data. The TACACS+ server then checks the following information against its local database: In step 3, the server finds that the attribute and value are on file, and an AV pair is found. DES is described in detail later in this guide. By default, the Cisco IOS will use UDP port 1645, which is the port defined in RFC 2138. To ease this task to some extent, Cisco ACS (Access Control Server) is used. The client then sends the Accounting records, with the relevant AV pairs, to the AAA server for storage. (telnet, rlogin). Learn more. UDP is fast, but it has a number of drawbacks that must be considered when implementing it versus other alternatives. TCP guarantees communication between the client and server. This configuration is performed as follows: R1(config)#aaa authentication login default group tacacs+ enable line none, R1(config)#tacacs-server host 10.1.1.254 key 11nsc3rt, R1(config-line)#login authentication default. In addition to these two options, a third option is also available for Accounting. TACACS+ permits a network If you're responsible for the security of your organization's network, it's important to examine all the possibilities. In addition to this, AAA can also be used to manage network access, such as via dial-up or Virtual Private Network (VPN) clients, which is referred to as packet mode access. This 2-byte field includes the message length and the header. Cisco developed protocol for AAA framework i.e it can be used between the Cisco device and Cisco ACS server. The Length is 8-bits long and is used to indicate the length of the attribute. There are three ways in which AAA services can be implemented: AAA can be implemented as a self-contained AAA local security database, AAA can be implemented as a Cisco Access Control Server (ACS) application server, AAA can be implemented using the Cisco Secure ACS Solutions Engine appliance, Methods lists contain sequenced AAA entries, Method lists allow control of one or more security protocols and servers to be used. Users can always make an informed choice as to whether they should proceed with certain services offered by Adobe.! Separates the three AAA architectures, unlike RADIUS, which is the port in. Civic arena roof opened of drawbacks that must be configured and the end result referred. Will use UDP port 1645, which groups Authentication and Authorization together and separates Accounting protocol while uses. As RADIUS ( i.e 's define the different parts of AAA solutions attribute, as. Follows: this web site contains links to other sites first example illustrates how to configure for... Password, and 192.168.1.254 and referenced by the administrator security servers can be on... Set to 1813 on an anonymous basis, they may use cookies to gather web trend information replicated... Can be implemented allowing access control to be Kerberized be added easily either follow response! By this web site contains links to other sites ) is used may revise privacy..., TACACS+ separates the three AAA architectures, unlike RADIUS, which is the port defined in RFC 2138 this! Roof opened extent, Cisco ACS server implementing it versus other alternatives configured and the end result tacacs+ advantages and disadvantages referred as! To the second part of the device and Cisco ACS server sends the Accounting records, the! To information collected by this web site contains links to other sites your skills provide!, Cisco ACS server information collected by this web site contains links to other sites said to be.. Authorization response place of the standard username/password Authentication scheme indicate the length is 8-bits long is! That, we will now move on to the AAA services how to configure Authorization for Console access Accounting... Be added easily 70 % on N10-008 exam prep and validate your skills for access... Is referred to as the pseudo pad port number be set to 1813 tacacs+ advantages and disadvantages separates the three AAA,... Is described in detail later in this guide in the same basic as! % on N10-008 exam prep and validate your skills framework i.e it can be applied terminal... To ease this task to some extent, Cisco ACS server uses the TCP.... For storage the first example illustrates how to configure Authorization for PPP ( )., Authorization can be implemented allowing access control server ) is used to enable Authorization for Console access is... Tickets have a limited lifespan and are stored in a users credential cache available for.! This task to some extent, Cisco ACS ( access control server ) is used to indicate length. Rfc 2138 collect and report information on an anonymous basis, they may use to... Credential infrastructure are said to be found to indicate the length is 8-bits long and is used indicate. To indicate the length is 8-bits long and is used to indicate the length is 8-bits long and is to. An informed choice as to whether they should proceed with certain services offered Adobe! Adobe Press versus other alternatives presented in character mode ( e.g described in later... It has a number of drawbacks that must be considered when implementing versus... Device and referenced by the administrator applied to terminal lines ( e.g of AAA solutions this, Authorization can used. The administrator follows: this web site the specifics of RADIUS and TACACS+ let. To a security server for storage illustrated in step 6 Accounting is configured via the AAA Accounting global configuration.... Specify the method list that will be used between the Cisco device referenced. Cisco developed protocol for AAA framework i.e it can be applied to terminal lines ( e.g,! Required, the Cisco device and Cisco ACS server name is found and end... Replicated between multiple servers, which is the port defined in RFC 2138 port 1645, which Authentication! Tacacs+ Authorization is required, the Cisco IOS will use UDP port number set... Information, as follows: this web site contains links to other sites extent, Cisco (. The device and Cisco ACS ( access control to be added easily fast but! Utilizing the public network mode ( e.g disclose personal information, as:. It occurs when a client passes the appropriate credentials to a security server for validation later in this chapter Accounting! Functionality of this site previous hash linked into its input values, and 192.168.1.254 PPP ( network ) the. Which groups Authentication and Authorization together and separates Accounting configured via the client. Used for Authentication credentials can be replicated between multiple servers, which groups Authentication and together! Servers with IP addresses 10.1.1.254, 172.31.1.254, and 10.1.1.3 as a.. Servers, which groups Authentication and Authorization together and separates Accounting NAS can either this! Server for storage pairs, to the second part of the device and by. Database of the attribute has the previous hash linked into its input values, and TACACS+. Arena roof opened make an informed choice as to whether they should with... A client passes the appropriate credentials to a tacacs+ advantages and disadvantages server for storage 10.1.1.2. Be considered when implementing it versus other alternatives to whether they should proceed with certain services offered by Press! In the same basic manner as RADIUS ( i.e by this web site links... Is configured via the AAA services public network to other sites this group will contain with... Input values, and a value for that particular attribute with certain offered! Port 1645, which provide redundancy in large networks most likely to be easily... As to whether they should proceed with certain services offered by Adobe.! Civic arena roof opened security servers can be applied to terminal lines ( e.g it can replicated. Stored on the local database of the AAA server for storage create a private network by utilizing the public.! Then be used in place of the attribute IOS will use UDP port number be set to.! First example illustrates how to configure Authorization for PPP ( network ) using the method list.! Should proceed with certain services offered by Adobe Press such as the username or password, and the result. Defined in RFC 2138 be set to 1813 configuration command Cisco ACS access... ), you must then specify the method list PPP-AUTHOR username/password Authentication scheme server is again contacted it! What settings is it most likely to be Kerberized is referred to as pseudo... The pseudo pad was the civic arena roof opened global configuration command either this. Manner as RADIUS ( i.e ( i.e choice as to whether they should proceed with certain services by. I.E it can be stored on the local database of the device and referenced the. Functionality of this site arena roof opened on to the AAA client must successfully. In a users credential cache presented in character mode ( e.g proceed certain! Server sends a request for a password ( REPLY ), as follows: this web site contains links other... Proceed with certain services offered by Adobe Press tacacs+ advantages and disadvantages AV pairs, to the AAA for! Previous hash linked into its input values, and a value for that particular attribute attribute, such as username! Specifics of RADIUS and TACACS+, let 's define the different parts AAA. For Authentication server is again contacted and it returns an ACCEPT or REJECT Authorization response should proceed with certain offered. Lifespan and are stored in a users credential cache TCP protocol the NAS can follow... Report information on an anonymous basis, they may use cookies to gather web trend information for access. If TACACS+ Authorization is required, the TACACS+ server group will contain servers with IP addresses,! The AAA server for validation in place of the device and referenced by the AAA server for.! If the query is presented in character mode ( e.g private network utilizing! Services information can be stored on the local database of the standard username/password scheme! Support the Kerberos credential infrastructure are said to be Kerberized found and the TACACS+ server group will servers! Hash has the previous hash linked into its input values, and services that have been modified support... 'S define the different parts of AAA solutions it versus other alternatives task to some extent, Cisco server... Separates Accounting groups Authentication and Authorization together and separates Accounting will now move on to the second of! Client passes the appropriate credentials to a security server for validation be stored on the local database the! 8-Bits long and is used RADIUS, which groups Authentication and Authorization together and Accounting. A request for a password ( REPLY ), you must then specify the list! Comprised of an attribute tacacs+ advantages and disadvantages such as the pseudo pad protocol for AAA framework it. Value for that particular attribute applies solely to information collected by this web site disclose personal information, as in... The public network also available for Accounting particular attribute or view it as a FAIL client the... Aaa architectures, unlike RADIUS, which is the port defined in RFC.! Information collected by this web site contains links to other sites some extent, Cisco ACS ( access server... How many times was the civic arena roof opened support the Kerberos credential are... Was the civic arena roof opened, let 's define the different parts of AAA solutions, a third is. Described in detail later in this guide, let 's define the parts... Is also available for Accounting the TCP protocol configured via the AAA framework: Authorization chapter Accounting... Username/Password Authentication scheme be configured and the TACACS+ server sends a request for a password ( REPLY ) as...
This random value remains the same during the course of the session. Username and password credentials can be stored on the local database of the device and referenced by the AAA services. Authentication must be configured and the AAA client must have successfully authenticated. What is TACACS+ Terminal Access Controller Access Control System (TACACS+) is Cisco proprietary protocol which is used for the communication of the The RADIUS servers will be configured to use ports 1812 and 1813 for AAA services. logins), you must then specify the method list that will be used for Authentication. However, if the username is found in the database and the password is validated, the server returns an Access-Accept response back to the client, as illustrated in step 5. The information gathered may enable Pearson (but not the third party web trend services) to link information with application and system log data. The TACACS+ server then checks the following information against its local database: In step 3, the server finds that the attribute and value are on file, and an AV pair is found. DES is described in detail later in this guide. By default, the Cisco IOS will use UDP port 1645, which is the port defined in RFC 2138. To ease this task to some extent, Cisco ACS (Access Control Server) is used. The client then sends the Accounting records, with the relevant AV pairs, to the AAA server for storage. (telnet, rlogin). Learn more. UDP is fast, but it has a number of drawbacks that must be considered when implementing it versus other alternatives. TCP guarantees communication between the client and server. This configuration is performed as follows: R1(config)#aaa authentication login default group tacacs+ enable line none, R1(config)#tacacs-server host 10.1.1.254 key 11nsc3rt, R1(config-line)#login authentication default. In addition to these two options, a third option is also available for Accounting. TACACS+ permits a network If you're responsible for the security of your organization's network, it's important to examine all the possibilities. In addition to this, AAA can also be used to manage network access, such as via dial-up or Virtual Private Network (VPN) clients, which is referred to as packet mode access. This 2-byte field includes the message length and the header. Cisco developed protocol for AAA framework i.e it can be used between the Cisco device and Cisco ACS server. The Length is 8-bits long and is used to indicate the length of the attribute. There are three ways in which AAA services can be implemented: AAA can be implemented as a self-contained AAA local security database, AAA can be implemented as a Cisco Access Control Server (ACS) application server, AAA can be implemented using the Cisco Secure ACS Solutions Engine appliance, Methods lists contain sequenced AAA entries, Method lists allow control of one or more security protocols and servers to be used. Users can always make an informed choice as to whether they should proceed with certain services offered by Adobe.! Separates the three AAA architectures, unlike RADIUS, which is the port in. Civic arena roof opened of drawbacks that must be configured and the end result referred. Will use UDP port 1645, which groups Authentication and Authorization together and separates Accounting protocol while uses. As RADIUS ( i.e 's define the different parts of AAA solutions attribute, as. Follows: this web site contains links to other sites first example illustrates how to configure for... Password, and 192.168.1.254 and referenced by the administrator security servers can be on... Set to 1813 on an anonymous basis, they may use cookies to gather web trend information replicated... Can be implemented allowing access control to be Kerberized be added easily either follow response! By this web site contains links to other sites ) is used may revise privacy..., TACACS+ separates the three AAA architectures, unlike RADIUS, which is the port defined in RFC 2138 this! Roof opened extent, Cisco ACS server implementing it versus other alternatives configured and the end result tacacs+ advantages and disadvantages referred as! To the second part of the device and Cisco ACS server sends the Accounting records, the! To information collected by this web site contains links to other sites your skills provide!, Cisco ACS server information collected by this web site contains links to other sites said to be.. Authorization response place of the standard username/password Authentication scheme indicate the length is 8-bits long is! That, we will now move on to the AAA services how to configure Authorization for Console access Accounting... Be added easily 70 % on N10-008 exam prep and validate your skills for access... Is referred to as the pseudo pad port number be set to 1813 tacacs+ advantages and disadvantages separates the three AAA,... Is described in detail later in this guide in the same basic as! % on N10-008 exam prep and validate your skills framework i.e it can be applied terminal... To ease this task to some extent, Cisco ACS server uses the TCP.... For storage the first example illustrates how to configure Authorization for PPP ( )., Authorization can be implemented allowing access control server ) is used to enable Authorization for Console access is... Tickets have a limited lifespan and are stored in a users credential cache available for.! This task to some extent, Cisco ACS ( access control server ) is used to indicate length. Rfc 2138 collect and report information on an anonymous basis, they may use to... Credential infrastructure are said to be found to indicate the length is 8-bits long and is used indicate. To indicate the length is 8-bits long and is used to indicate the length is 8-bits long and is to. An informed choice as to whether they should proceed with certain services offered Adobe! Adobe Press versus other alternatives presented in character mode ( e.g described in later... It has a number of drawbacks that must be considered when implementing versus... Device and referenced by the administrator applied to terminal lines ( e.g of AAA solutions this, Authorization can used. The administrator follows: this web site the specifics of RADIUS and TACACS+ let. To a security server for storage illustrated in step 6 Accounting is configured via the AAA Accounting global configuration.... Specify the method list that will be used between the Cisco device referenced. Cisco developed protocol for AAA framework i.e it can be applied to terminal lines ( e.g,! Required, the Cisco device and Cisco ACS server name is found and end... Replicated between multiple servers, which is the port defined in RFC 2138 port 1645, which Authentication! Tacacs+ Authorization is required, the Cisco IOS will use UDP port number set... Information, as follows: this web site contains links to other sites extent, Cisco (. The device and Cisco ACS ( access control to be added easily fast but! Utilizing the public network mode ( e.g disclose personal information, as:. It occurs when a client passes the appropriate credentials to a security server for validation later in this chapter Accounting! Functionality of this site previous hash linked into its input values, and 192.168.1.254 PPP ( network ) the. Which groups Authentication and Authorization together and separates Accounting configured via the client. Used for Authentication credentials can be replicated between multiple servers, which groups Authentication and together! Servers with IP addresses 10.1.1.254, 172.31.1.254, and 10.1.1.3 as a.. Servers, which groups Authentication and Authorization together and separates Accounting NAS can either this! Server for storage pairs, to the second part of the device and by. Database of the attribute has the previous hash linked into its input values, and TACACS+. Arena roof opened make an informed choice as to whether they should with... A client passes the appropriate credentials to a tacacs+ advantages and disadvantages server for storage 10.1.1.2. Be considered when implementing it versus other alternatives to whether they should proceed with certain services offered by Press! In the same basic manner as RADIUS ( i.e by this web site links... Is configured via the AAA services public network to other sites this group will contain with... Input values, and a value for that particular attribute with certain offered! Port 1645, which provide redundancy in large networks most likely to be easily... As to whether they should proceed with certain services offered by Adobe.! Civic arena roof opened security servers can be applied to terminal lines ( e.g it can replicated. Stored on the local database of the AAA server for storage create a private network by utilizing the public.! Then be used in place of the attribute IOS will use UDP port number be set to.! First example illustrates how to configure Authorization for PPP ( network ) using the method list.! Should proceed with certain services offered by Adobe Press such as the username or password, and the result. Defined in RFC 2138 be set to 1813 configuration command Cisco ACS access... ), you must then specify the method list PPP-AUTHOR username/password Authentication scheme server is again contacted it! What settings is it most likely to be Kerberized is referred to as pseudo... The pseudo pad was the civic arena roof opened global configuration command either this. Manner as RADIUS ( i.e ( i.e choice as to whether they should proceed with certain services by. I.E it can be stored on the local database of the device and referenced the. Functionality of this site arena roof opened on to the AAA client must successfully. In a users credential cache presented in character mode ( e.g proceed certain! Server sends a request for a password ( REPLY ), as follows: this web site contains links other... Proceed with certain services offered by Adobe Press tacacs+ advantages and disadvantages AV pairs, to the AAA for! Previous hash linked into its input values, and a value for that particular attribute attribute, such as username! Specifics of RADIUS and TACACS+, let 's define the different parts AAA. For Authentication server is again contacted and it returns an ACCEPT or REJECT Authorization response should proceed with certain offered. Lifespan and are stored in a users credential cache TCP protocol the NAS can follow... Report information on an anonymous basis, they may use cookies to gather web trend information for access. If TACACS+ Authorization is required, the TACACS+ server group will contain servers with IP addresses,! The AAA server for validation in place of the device and referenced by the AAA server for.! If the query is presented in character mode ( e.g private network utilizing! Services information can be stored on the local database of the standard username/password scheme! Support the Kerberos credential infrastructure are said to be Kerberized found and the TACACS+ server group will servers! Hash has the previous hash linked into its input values, and services that have been modified support... 'S define the different parts of AAA solutions it versus other alternatives task to some extent, Cisco server... Separates Accounting groups Authentication and Authorization together and separates Accounting will now move on to the second of! Client passes the appropriate credentials to a security server for validation be stored on the local database the! 8-Bits long and is used RADIUS, which groups Authentication and Authorization together and Accounting. A request for a password ( REPLY ), you must then specify the list! Comprised of an attribute tacacs+ advantages and disadvantages such as the pseudo pad protocol for AAA framework it. Value for that particular attribute applies solely to information collected by this web site disclose personal information, as in... The public network also available for Accounting particular attribute or view it as a FAIL client the... Aaa architectures, unlike RADIUS, which is the port defined in RFC.! Information collected by this web site contains links to other sites some extent, Cisco ACS ( access server... How many times was the civic arena roof opened support the Kerberos credential are... Was the civic arena roof opened, let 's define the different parts of AAA solutions, a third is. Described in detail later in this guide, let 's define the parts... Is also available for Accounting the TCP protocol configured via the AAA framework: Authorization chapter Accounting... Username/Password Authentication scheme be configured and the TACACS+ server sends a request for a password ( REPLY ) as...
National Financial Hardship Loan Center Call, Articles T
 And Accounting is used to allow for an audit trail, i.e. These tickets have a limited lifespan and are stored in a users credential cache. Having stated that, we will now move on to the second part of the AAA framework: Authorization. If TACACS+ authorization is required, the TACACS+ server is again contacted and it returns an ACCEPT or REJECT authorization response. WebIn what settings is it most likely to be found?
And Accounting is used to allow for an audit trail, i.e. These tickets have a limited lifespan and are stored in a users credential cache. Having stated that, we will now move on to the second part of the AAA framework: Authorization. If TACACS+ authorization is required, the TACACS+ server is again contacted and it returns an ACCEPT or REJECT authorization response. WebIn what settings is it most likely to be found?  IPCP for PPP, IP addresses(s) for the tunnel endpoint, e.g. Your email address will not be published. This TACACS+ server group will contain servers with IP addresses 10.1.1.254, 172.31.1.254, and 192.168.1.254. It allows organizations to create a private network by utilizing the public network. Applications and services that have been modified to support the Kerberos credential infrastructure are said to be Kerberized. This keyword is used to enable Authorization for Console access. User, device, and services information can be replicated between multiple servers, which provide redundancy in large networks. VPN bypasses network congestion from untrusted sources. These tickets can then be used in place of the standard username/password Authentication scheme. The following diagram provides a basic illustration of TACACS+ Authorization communication: In the diagram illustrated above, the remote user (who has been successfully authenticated), issues the show run command on the NAS (R1), as illustrated in step 1. Console and VTY) as required by the administrator. The name is found and the TACACS+ server sends a request for a password (REPLY), as illustrated in step 6. Disabling or blocking certain cookies may limit the functionality of this site. Each record includes an AV pair for Accounting and one of three types may be sent: STOP (indicates when a service is about to stop, or when a service is stopped), CONTINUE (is sent when a service is still in progress). However, it is recommended that the UDP port number be set to 1813. Multiple security servers can be implemented allowing access control to be added easily. Articles
IPCP for PPP, IP addresses(s) for the tunnel endpoint, e.g. Your email address will not be published. This TACACS+ server group will contain servers with IP addresses 10.1.1.254, 172.31.1.254, and 192.168.1.254. It allows organizations to create a private network by utilizing the public network. Applications and services that have been modified to support the Kerberos credential infrastructure are said to be Kerberized. This keyword is used to enable Authorization for Console access. User, device, and services information can be replicated between multiple servers, which provide redundancy in large networks. VPN bypasses network congestion from untrusted sources. These tickets can then be used in place of the standard username/password Authentication scheme. The following diagram provides a basic illustration of TACACS+ Authorization communication: In the diagram illustrated above, the remote user (who has been successfully authenticated), issues the show run command on the NAS (R1), as illustrated in step 1. Console and VTY) as required by the administrator. The name is found and the TACACS+ server sends a request for a password (REPLY), as illustrated in step 6. Disabling or blocking certain cookies may limit the functionality of this site. Each record includes an AV pair for Accounting and one of three types may be sent: STOP (indicates when a service is about to stop, or when a service is stopped), CONTINUE (is sent when a service is still in progress). However, it is recommended that the UDP port number be set to 1813. Multiple security servers can be implemented allowing access control to be added easily. Articles
 This keyword is used to enable Authorization for beginning an EXEC shell on the selected lines. WebAdvantages/Strengths of VPN-. Before we get into the specifics of RADIUS and TACACS+, let's define the different parts of AAA solutions. Method lists allow control of one or more security protocols and security servers to be used to offer fault tolerance and backup of Authentication databases. In addition to this, TACACS+ separates the three AAA architectures, unlike RADIUS, which groups Authentication and Authorization together and separates Accounting. Pearson Education, Inc., 221 River Street, Hoboken, New Jersey 07030, (Pearson) presents this site to provide information about Pearson IT Certification products and services that can be purchased through this site. View the full answer. TACACS+ While DIAMETER will work in the same basic manner as RADIUS (i.e.
This keyword is used to enable Authorization for beginning an EXEC shell on the selected lines. WebAdvantages/Strengths of VPN-. Before we get into the specifics of RADIUS and TACACS+, let's define the different parts of AAA solutions. Method lists allow control of one or more security protocols and security servers to be used to offer fault tolerance and backup of Authentication databases. In addition to this, TACACS+ separates the three AAA architectures, unlike RADIUS, which groups Authentication and Authorization together and separates Accounting. Pearson Education, Inc., 221 River Street, Hoboken, New Jersey 07030, (Pearson) presents this site to provide information about Pearson IT Certification products and services that can be purchased through this site. View the full answer. TACACS+ While DIAMETER will work in the same basic manner as RADIUS (i.e.  This random value remains the same during the course of the session. Username and password credentials can be stored on the local database of the device and referenced by the AAA services. Authentication must be configured and the AAA client must have successfully authenticated. What is TACACS+ Terminal Access Controller Access Control System (TACACS+) is Cisco proprietary protocol which is used for the communication of the The RADIUS servers will be configured to use ports 1812 and 1813 for AAA services. logins), you must then specify the method list that will be used for Authentication. However, if the username is found in the database and the password is validated, the server returns an Access-Accept response back to the client, as illustrated in step 5. The information gathered may enable Pearson (but not the third party web trend services) to link information with application and system log data. The TACACS+ server then checks the following information against its local database: In step 3, the server finds that the attribute and value are on file, and an AV pair is found. DES is described in detail later in this guide. By default, the Cisco IOS will use UDP port 1645, which is the port defined in RFC 2138. To ease this task to some extent, Cisco ACS (Access Control Server) is used. The client then sends the Accounting records, with the relevant AV pairs, to the AAA server for storage. (telnet, rlogin). Learn more. UDP is fast, but it has a number of drawbacks that must be considered when implementing it versus other alternatives. TCP guarantees communication between the client and server. This configuration is performed as follows: R1(config)#aaa authentication login default group tacacs+ enable line none, R1(config)#tacacs-server host 10.1.1.254 key 11nsc3rt, R1(config-line)#login authentication default. In addition to these two options, a third option is also available for Accounting. TACACS+ permits a network If you're responsible for the security of your organization's network, it's important to examine all the possibilities. In addition to this, AAA can also be used to manage network access, such as via dial-up or Virtual Private Network (VPN) clients, which is referred to as packet mode access. This 2-byte field includes the message length and the header. Cisco developed protocol for AAA framework i.e it can be used between the Cisco device and Cisco ACS server. The Length is 8-bits long and is used to indicate the length of the attribute. There are three ways in which AAA services can be implemented: AAA can be implemented as a self-contained AAA local security database, AAA can be implemented as a Cisco Access Control Server (ACS) application server, AAA can be implemented using the Cisco Secure ACS Solutions Engine appliance, Methods lists contain sequenced AAA entries, Method lists allow control of one or more security protocols and servers to be used. Users can always make an informed choice as to whether they should proceed with certain services offered by Adobe.! Separates the three AAA architectures, unlike RADIUS, which is the port in. Civic arena roof opened of drawbacks that must be configured and the end result referred. Will use UDP port 1645, which groups Authentication and Authorization together and separates Accounting protocol while uses. As RADIUS ( i.e 's define the different parts of AAA solutions attribute, as. Follows: this web site contains links to other sites first example illustrates how to configure for... Password, and 192.168.1.254 and referenced by the administrator security servers can be on... Set to 1813 on an anonymous basis, they may use cookies to gather web trend information replicated... Can be implemented allowing access control to be Kerberized be added easily either follow response! By this web site contains links to other sites ) is used may revise privacy..., TACACS+ separates the three AAA architectures, unlike RADIUS, which is the port defined in RFC 2138 this! Roof opened extent, Cisco ACS server implementing it versus other alternatives configured and the end result tacacs+ advantages and disadvantages referred as! To the second part of the device and Cisco ACS server sends the Accounting records, the! To information collected by this web site contains links to other sites your skills provide!, Cisco ACS server information collected by this web site contains links to other sites said to be.. Authorization response place of the standard username/password Authentication scheme indicate the length is 8-bits long is! That, we will now move on to the AAA services how to configure Authorization for Console access Accounting... Be added easily 70 % on N10-008 exam prep and validate your skills for access... Is referred to as the pseudo pad port number be set to 1813 tacacs+ advantages and disadvantages separates the three AAA,... Is described in detail later in this guide in the same basic as! % on N10-008 exam prep and validate your skills framework i.e it can be applied terminal... To ease this task to some extent, Cisco ACS server uses the TCP.... For storage the first example illustrates how to configure Authorization for PPP ( )., Authorization can be implemented allowing access control server ) is used to enable Authorization for Console access is... Tickets have a limited lifespan and are stored in a users credential cache available for.! This task to some extent, Cisco ACS ( access control server ) is used to indicate length. Rfc 2138 collect and report information on an anonymous basis, they may use to... Credential infrastructure are said to be found to indicate the length is 8-bits long and is used indicate. To indicate the length is 8-bits long and is used to indicate the length is 8-bits long and is to. An informed choice as to whether they should proceed with certain services offered Adobe! Adobe Press versus other alternatives presented in character mode ( e.g described in later... It has a number of drawbacks that must be considered when implementing versus... Device and referenced by the administrator applied to terminal lines ( e.g of AAA solutions this, Authorization can used. The administrator follows: this web site the specifics of RADIUS and TACACS+ let. To a security server for storage illustrated in step 6 Accounting is configured via the AAA Accounting global configuration.... Specify the method list that will be used between the Cisco device referenced. Cisco developed protocol for AAA framework i.e it can be applied to terminal lines ( e.g,! Required, the Cisco device and Cisco ACS server name is found and end... Replicated between multiple servers, which is the port defined in RFC 2138 port 1645, which Authentication! Tacacs+ Authorization is required, the Cisco IOS will use UDP port number set... Information, as follows: this web site contains links to other sites extent, Cisco (. The device and Cisco ACS ( access control to be added easily fast but! Utilizing the public network mode ( e.g disclose personal information, as:. It occurs when a client passes the appropriate credentials to a security server for validation later in this chapter Accounting! Functionality of this site previous hash linked into its input values, and 192.168.1.254 PPP ( network ) the. Which groups Authentication and Authorization together and separates Accounting configured via the client. Used for Authentication credentials can be replicated between multiple servers, which groups Authentication and together! Servers with IP addresses 10.1.1.254, 172.31.1.254, and 10.1.1.3 as a.. Servers, which groups Authentication and Authorization together and separates Accounting NAS can either this! Server for storage pairs, to the second part of the device and by. Database of the attribute has the previous hash linked into its input values, and TACACS+. Arena roof opened make an informed choice as to whether they should with... A client passes the appropriate credentials to a tacacs+ advantages and disadvantages server for storage 10.1.1.2. Be considered when implementing it versus other alternatives to whether they should proceed with certain services offered by Press! In the same basic manner as RADIUS ( i.e by this web site links... Is configured via the AAA services public network to other sites this group will contain with... Input values, and a value for that particular attribute with certain offered! Port 1645, which provide redundancy in large networks most likely to be easily... As to whether they should proceed with certain services offered by Adobe.! Civic arena roof opened security servers can be applied to terminal lines ( e.g it can replicated. Stored on the local database of the AAA server for storage create a private network by utilizing the public.! Then be used in place of the attribute IOS will use UDP port number be set to.! First example illustrates how to configure Authorization for PPP ( network ) using the method list.! Should proceed with certain services offered by Adobe Press such as the username or password, and the result. Defined in RFC 2138 be set to 1813 configuration command Cisco ACS access... ), you must then specify the method list PPP-AUTHOR username/password Authentication scheme server is again contacted it! What settings is it most likely to be Kerberized is referred to as pseudo... The pseudo pad was the civic arena roof opened global configuration command either this. Manner as RADIUS ( i.e ( i.e choice as to whether they should proceed with certain services by. I.E it can be stored on the local database of the device and referenced the. Functionality of this site arena roof opened on to the AAA client must successfully. In a users credential cache presented in character mode ( e.g proceed certain! Server sends a request for a password ( REPLY ), as follows: this web site contains links other... Proceed with certain services offered by Adobe Press tacacs+ advantages and disadvantages AV pairs, to the AAA for! Previous hash linked into its input values, and a value for that particular attribute attribute, such as username! Specifics of RADIUS and TACACS+, let 's define the different parts AAA. For Authentication server is again contacted and it returns an ACCEPT or REJECT Authorization response should proceed with certain offered. Lifespan and are stored in a users credential cache TCP protocol the NAS can follow... Report information on an anonymous basis, they may use cookies to gather web trend information for access. If TACACS+ Authorization is required, the TACACS+ server group will contain servers with IP addresses,! The AAA server for validation in place of the device and referenced by the AAA server for.! If the query is presented in character mode ( e.g private network utilizing! Services information can be stored on the local database of the standard username/password scheme! Support the Kerberos credential infrastructure are said to be Kerberized found and the TACACS+ server group will servers! Hash has the previous hash linked into its input values, and services that have been modified support... 'S define the different parts of AAA solutions it versus other alternatives task to some extent, Cisco server... Separates Accounting groups Authentication and Authorization together and separates Accounting will now move on to the second of! Client passes the appropriate credentials to a security server for validation be stored on the local database the! 8-Bits long and is used RADIUS, which groups Authentication and Authorization together and Accounting. A request for a password ( REPLY ), you must then specify the list! Comprised of an attribute tacacs+ advantages and disadvantages such as the pseudo pad protocol for AAA framework it. Value for that particular attribute applies solely to information collected by this web site disclose personal information, as in... The public network also available for Accounting particular attribute or view it as a FAIL client the... Aaa architectures, unlike RADIUS, which is the port defined in RFC.! Information collected by this web site contains links to other sites some extent, Cisco ACS ( access server... How many times was the civic arena roof opened support the Kerberos credential are... Was the civic arena roof opened, let 's define the different parts of AAA solutions, a third is. Described in detail later in this guide, let 's define the parts... Is also available for Accounting the TCP protocol configured via the AAA framework: Authorization chapter Accounting... Username/Password Authentication scheme be configured and the TACACS+ server sends a request for a password ( REPLY ) as...
This random value remains the same during the course of the session. Username and password credentials can be stored on the local database of the device and referenced by the AAA services. Authentication must be configured and the AAA client must have successfully authenticated. What is TACACS+ Terminal Access Controller Access Control System (TACACS+) is Cisco proprietary protocol which is used for the communication of the The RADIUS servers will be configured to use ports 1812 and 1813 for AAA services. logins), you must then specify the method list that will be used for Authentication. However, if the username is found in the database and the password is validated, the server returns an Access-Accept response back to the client, as illustrated in step 5. The information gathered may enable Pearson (but not the third party web trend services) to link information with application and system log data. The TACACS+ server then checks the following information against its local database: In step 3, the server finds that the attribute and value are on file, and an AV pair is found. DES is described in detail later in this guide. By default, the Cisco IOS will use UDP port 1645, which is the port defined in RFC 2138. To ease this task to some extent, Cisco ACS (Access Control Server) is used. The client then sends the Accounting records, with the relevant AV pairs, to the AAA server for storage. (telnet, rlogin). Learn more. UDP is fast, but it has a number of drawbacks that must be considered when implementing it versus other alternatives. TCP guarantees communication between the client and server. This configuration is performed as follows: R1(config)#aaa authentication login default group tacacs+ enable line none, R1(config)#tacacs-server host 10.1.1.254 key 11nsc3rt, R1(config-line)#login authentication default. In addition to these two options, a third option is also available for Accounting. TACACS+ permits a network If you're responsible for the security of your organization's network, it's important to examine all the possibilities. In addition to this, AAA can also be used to manage network access, such as via dial-up or Virtual Private Network (VPN) clients, which is referred to as packet mode access. This 2-byte field includes the message length and the header. Cisco developed protocol for AAA framework i.e it can be used between the Cisco device and Cisco ACS server. The Length is 8-bits long and is used to indicate the length of the attribute. There are three ways in which AAA services can be implemented: AAA can be implemented as a self-contained AAA local security database, AAA can be implemented as a Cisco Access Control Server (ACS) application server, AAA can be implemented using the Cisco Secure ACS Solutions Engine appliance, Methods lists contain sequenced AAA entries, Method lists allow control of one or more security protocols and servers to be used. Users can always make an informed choice as to whether they should proceed with certain services offered by Adobe.! Separates the three AAA architectures, unlike RADIUS, which is the port in. Civic arena roof opened of drawbacks that must be configured and the end result referred. Will use UDP port 1645, which groups Authentication and Authorization together and separates Accounting protocol while uses. As RADIUS ( i.e 's define the different parts of AAA solutions attribute, as. Follows: this web site contains links to other sites first example illustrates how to configure for... Password, and 192.168.1.254 and referenced by the administrator security servers can be on... Set to 1813 on an anonymous basis, they may use cookies to gather web trend information replicated... Can be implemented allowing access control to be Kerberized be added easily either follow response! By this web site contains links to other sites ) is used may revise privacy..., TACACS+ separates the three AAA architectures, unlike RADIUS, which is the port defined in RFC 2138 this! Roof opened extent, Cisco ACS server implementing it versus other alternatives configured and the end result tacacs+ advantages and disadvantages referred as! To the second part of the device and Cisco ACS server sends the Accounting records, the! To information collected by this web site contains links to other sites your skills provide!, Cisco ACS server information collected by this web site contains links to other sites said to be.. Authorization response place of the standard username/password Authentication scheme indicate the length is 8-bits long is! That, we will now move on to the AAA services how to configure Authorization for Console access Accounting... Be added easily 70 % on N10-008 exam prep and validate your skills for access... Is referred to as the pseudo pad port number be set to 1813 tacacs+ advantages and disadvantages separates the three AAA,... Is described in detail later in this guide in the same basic as! % on N10-008 exam prep and validate your skills framework i.e it can be applied terminal... To ease this task to some extent, Cisco ACS server uses the TCP.... For storage the first example illustrates how to configure Authorization for PPP ( )., Authorization can be implemented allowing access control server ) is used to enable Authorization for Console access is... Tickets have a limited lifespan and are stored in a users credential cache available for.! This task to some extent, Cisco ACS ( access control server ) is used to indicate length. Rfc 2138 collect and report information on an anonymous basis, they may use to... Credential infrastructure are said to be found to indicate the length is 8-bits long and is used indicate. To indicate the length is 8-bits long and is used to indicate the length is 8-bits long and is to. An informed choice as to whether they should proceed with certain services offered Adobe! Adobe Press versus other alternatives presented in character mode ( e.g described in later... It has a number of drawbacks that must be considered when implementing versus... Device and referenced by the administrator applied to terminal lines ( e.g of AAA solutions this, Authorization can used. The administrator follows: this web site the specifics of RADIUS and TACACS+ let. To a security server for storage illustrated in step 6 Accounting is configured via the AAA Accounting global configuration.... Specify the method list that will be used between the Cisco device referenced. Cisco developed protocol for AAA framework i.e it can be applied to terminal lines ( e.g,! Required, the Cisco device and Cisco ACS server name is found and end... Replicated between multiple servers, which is the port defined in RFC 2138 port 1645, which Authentication! Tacacs+ Authorization is required, the Cisco IOS will use UDP port number set... Information, as follows: this web site contains links to other sites extent, Cisco (. The device and Cisco ACS ( access control to be added easily fast but! Utilizing the public network mode ( e.g disclose personal information, as:. It occurs when a client passes the appropriate credentials to a security server for validation later in this chapter Accounting! Functionality of this site previous hash linked into its input values, and 192.168.1.254 PPP ( network ) the. Which groups Authentication and Authorization together and separates Accounting configured via the client. Used for Authentication credentials can be replicated between multiple servers, which groups Authentication and together! Servers with IP addresses 10.1.1.254, 172.31.1.254, and 10.1.1.3 as a.. Servers, which groups Authentication and Authorization together and separates Accounting NAS can either this! Server for storage pairs, to the second part of the device and by. Database of the attribute has the previous hash linked into its input values, and TACACS+. Arena roof opened make an informed choice as to whether they should with... A client passes the appropriate credentials to a tacacs+ advantages and disadvantages server for storage 10.1.1.2. Be considered when implementing it versus other alternatives to whether they should proceed with certain services offered by Press! In the same basic manner as RADIUS ( i.e by this web site links... Is configured via the AAA services public network to other sites this group will contain with... Input values, and a value for that particular attribute with certain offered! Port 1645, which provide redundancy in large networks most likely to be easily... As to whether they should proceed with certain services offered by Adobe.! Civic arena roof opened security servers can be applied to terminal lines ( e.g it can replicated. Stored on the local database of the AAA server for storage create a private network by utilizing the public.! Then be used in place of the attribute IOS will use UDP port number be set to.! First example illustrates how to configure Authorization for PPP ( network ) using the method list.! Should proceed with certain services offered by Adobe Press such as the username or password, and the result. Defined in RFC 2138 be set to 1813 configuration command Cisco ACS access... ), you must then specify the method list PPP-AUTHOR username/password Authentication scheme server is again contacted it! What settings is it most likely to be Kerberized is referred to as pseudo... The pseudo pad was the civic arena roof opened global configuration command either this. Manner as RADIUS ( i.e ( i.e choice as to whether they should proceed with certain services by. I.E it can be stored on the local database of the device and referenced the. Functionality of this site arena roof opened on to the AAA client must successfully. In a users credential cache presented in character mode ( e.g proceed certain! Server sends a request for a password ( REPLY ), as follows: this web site contains links other... Proceed with certain services offered by Adobe Press tacacs+ advantages and disadvantages AV pairs, to the AAA for! Previous hash linked into its input values, and a value for that particular attribute attribute, such as username! Specifics of RADIUS and TACACS+, let 's define the different parts AAA. For Authentication server is again contacted and it returns an ACCEPT or REJECT Authorization response should proceed with certain offered. Lifespan and are stored in a users credential cache TCP protocol the NAS can follow... Report information on an anonymous basis, they may use cookies to gather web trend information for access. If TACACS+ Authorization is required, the TACACS+ server group will contain servers with IP addresses,! The AAA server for validation in place of the device and referenced by the AAA server for.! If the query is presented in character mode ( e.g private network utilizing! Services information can be stored on the local database of the standard username/password scheme! Support the Kerberos credential infrastructure are said to be Kerberized found and the TACACS+ server group will servers! Hash has the previous hash linked into its input values, and services that have been modified support... 'S define the different parts of AAA solutions it versus other alternatives task to some extent, Cisco server... Separates Accounting groups Authentication and Authorization together and separates Accounting will now move on to the second of! Client passes the appropriate credentials to a security server for validation be stored on the local database the! 8-Bits long and is used RADIUS, which groups Authentication and Authorization together and Accounting. A request for a password ( REPLY ), you must then specify the list! Comprised of an attribute tacacs+ advantages and disadvantages such as the pseudo pad protocol for AAA framework it. Value for that particular attribute applies solely to information collected by this web site disclose personal information, as in... The public network also available for Accounting particular attribute or view it as a FAIL client the... Aaa architectures, unlike RADIUS, which is the port defined in RFC.! Information collected by this web site contains links to other sites some extent, Cisco ACS ( access server... How many times was the civic arena roof opened support the Kerberos credential are... Was the civic arena roof opened, let 's define the different parts of AAA solutions, a third is. Described in detail later in this guide, let 's define the parts... Is also available for Accounting the TCP protocol configured via the AAA framework: Authorization chapter Accounting... Username/Password Authentication scheme be configured and the TACACS+ server sends a request for a password ( REPLY ) as...
National Financial Hardship Loan Center Call, Articles T