Another issue with the NIST framework, and another area in which the framework is fast becoming obsolete, is cloud computing. The fifth step is to change your default settings and credentials that may expose your network to hackers.  For each of the five functions, there are categories that are actually specific challenges or tasks that you must carry out.
For each of the five functions, there are categories that are actually specific challenges or tasks that you must carry out.  This button displays the currently selected search type.
This button displays the currently selected search type.  A firewall is a software or hardware device that acts as a barrier between your network and the internet. Not following the NIST guidelines presents more of a liability. Cyberattacks are becoming more widespread and complex, and fighting these attacks are becoming much more difficult. Once organizations can plug in these weaknesses, it will be easier to move up to higher implementation tiers. You can liken profiles to an executive summary of everything an organization has done for the NIST Cybersecurity Framework. The NIST Cybersecurity Framework Core is a collection of tasks, results, and references designed to provide businesses a thorough method of managing their cybersecurity risks. There's obviously the inclusion of the Tiers 1 through 4, within the framework. "The first concern is that it is voluntary, and money does speak loudly. Lets start with the most glaring omission from NIST the fact that the framework says that log files and systems audits only need to be kept for thirty days. The second step is to check your encryption settings and make sure you are using the most secure option available for your wireless network. And so, when I go to a company, that's trying use the framework, I'm not going to be looking to them, to say "Show me your particular document, that satisfies this requirement." The higher the tier, the more compliant you are. Organizations are using the US National Institute of Standards and Technology (NIST) Cybersecurity Framework to customize their assessment of controls related to cyber or cloud to mitigate the threats and other risk impacting the network assets or enterprise IT structure, COBIT, and other frameworks. stream
Mass.gov is a registered service mark of the Commonwealth of Massachusetts. The 'Identify' section outlines associated risks. Network Computing is part of the Informa Tech Division of Informa PLC.
A firewall is a software or hardware device that acts as a barrier between your network and the internet. Not following the NIST guidelines presents more of a liability. Cyberattacks are becoming more widespread and complex, and fighting these attacks are becoming much more difficult. Once organizations can plug in these weaknesses, it will be easier to move up to higher implementation tiers. You can liken profiles to an executive summary of everything an organization has done for the NIST Cybersecurity Framework. The NIST Cybersecurity Framework Core is a collection of tasks, results, and references designed to provide businesses a thorough method of managing their cybersecurity risks. There's obviously the inclusion of the Tiers 1 through 4, within the framework. "The first concern is that it is voluntary, and money does speak loudly. Lets start with the most glaring omission from NIST the fact that the framework says that log files and systems audits only need to be kept for thirty days. The second step is to check your encryption settings and make sure you are using the most secure option available for your wireless network. And so, when I go to a company, that's trying use the framework, I'm not going to be looking to them, to say "Show me your particular document, that satisfies this requirement." The higher the tier, the more compliant you are. Organizations are using the US National Institute of Standards and Technology (NIST) Cybersecurity Framework to customize their assessment of controls related to cyber or cloud to mitigate the threats and other risk impacting the network assets or enterprise IT structure, COBIT, and other frameworks. stream
Mass.gov is a registered service mark of the Commonwealth of Massachusetts. The 'Identify' section outlines associated risks. Network Computing is part of the Informa Tech Division of Informa PLC.  Contact us to learn which security framework is best for your organization and how CyberStrong can streamline compliance and risk assessments. Thanks for watching this video. We work to advance government policies that protect consumers and promote competition. Encryption is the process of scrambling your data so that only authorized devices can read it. This is further divided into four different elements: Functions. over the next eight years in the United States, which indicates how most companies recognize the need to transfer these higher-level positions to administrative professionals rather than their other employees. Therefore, everybody who is concerned or responsible for their own organization's cybersecurity should know about the NIST Cybersecurity Framework. Instead, he said the document is focused on results for critical infrastructure providers, and its reliance on existing standards like NIST 800-53 and COBIT 5 should be seen as a positive. WebLimitations of Cybersecurity Frameworks that Cybersecurity Specialists must Understand to Reduce Cybersecurity Breaches Hitchcox, Zachery . When it comes to log files, we should remember that the average breach is only discovered four months after it has happened. Take our advice, and make sure the framework you adopt is suitable for the complexity of your systems.
Contact us to learn which security framework is best for your organization and how CyberStrong can streamline compliance and risk assessments. Thanks for watching this video. We work to advance government policies that protect consumers and promote competition. Encryption is the process of scrambling your data so that only authorized devices can read it. This is further divided into four different elements: Functions. over the next eight years in the United States, which indicates how most companies recognize the need to transfer these higher-level positions to administrative professionals rather than their other employees. Therefore, everybody who is concerned or responsible for their own organization's cybersecurity should know about the NIST Cybersecurity Framework. Instead, he said the document is focused on results for critical infrastructure providers, and its reliance on existing standards like NIST 800-53 and COBIT 5 should be seen as a positive. WebLimitations of Cybersecurity Frameworks that Cybersecurity Specialists must Understand to Reduce Cybersecurity Breaches Hitchcox, Zachery . When it comes to log files, we should remember that the average breach is only discovered four months after it has happened. Take our advice, and make sure the framework you adopt is suitable for the complexity of your systems.  2) Protect - The protect function directs companies to evaluate existing cybersecurity procedures and processes to ensure they can safeguard the organizations assets. Again, this matters because companies who want to take cybersecurity seriously but who lack the in-house resources to develop their own systems are faced with contradictory advice. The CSF assumes an outdated and more discreet way of working. Like or react to bring the conversation to your network. NIST recommends that companies use what it calls RBAC Role-Based Access Control to secure systems. The different sets of policies, guidelines, best practices, and technologies used in cybersecurity gives rise to yet another problem: organizations are not able to share information about attacks. You can use tools like Nmap, Wireshark, or NetSpot to scan your network and identify the MAC addresses, IP addresses, and SSIDs of all devices. WebPros, cons and the advantages each framework holds over the other and how an organization would select an appropriate framework between CSF and ISO 27001 have been discussed along with a detailed comparison of how major security controls framework/guidelines like NIST SP 800-53, CIS Top-20 and ISO 27002 can be mapped back to each. This is the framework," which petrified me, because we don't need any more checklists. Thank U, Next. Because of the rise of cheap, unlimited cloud storage options (more on which in a moment), its possible to store years worth of logs without running into resource limitations.
2) Protect - The protect function directs companies to evaluate existing cybersecurity procedures and processes to ensure they can safeguard the organizations assets. Again, this matters because companies who want to take cybersecurity seriously but who lack the in-house resources to develop their own systems are faced with contradictory advice. The CSF assumes an outdated and more discreet way of working. Like or react to bring the conversation to your network. NIST recommends that companies use what it calls RBAC Role-Based Access Control to secure systems. The different sets of policies, guidelines, best practices, and technologies used in cybersecurity gives rise to yet another problem: organizations are not able to share information about attacks. You can use tools like Nmap, Wireshark, or NetSpot to scan your network and identify the MAC addresses, IP addresses, and SSIDs of all devices. WebPros, cons and the advantages each framework holds over the other and how an organization would select an appropriate framework between CSF and ISO 27001 have been discussed along with a detailed comparison of how major security controls framework/guidelines like NIST SP 800-53, CIS Top-20 and ISO 27002 can be mapped back to each. This is the framework," which petrified me, because we don't need any more checklists. Thank U, Next. Because of the rise of cheap, unlimited cloud storage options (more on which in a moment), its possible to store years worth of logs without running into resource limitations.  The National Institute of Standards and Technology (NIST) is a part of the U.S. Department of Commerce. However, while managing cybersecurity risk contributes to The fourth step is to use a firewall to filter and block any unwanted or malicious traffic that may try to enter or leave your network. Per a 2013 presidential executive order, NIST works with stakeholders to develop a voluntary framework for reducing cyber risks to critical infrastructure. NIST SP 800-171 So, I think that's a way to encourage people to realize that that's how they can move forward. Hayden: Well, I highly respect Mike. The site is secure. The profiles can also help business managers see how each function, category, or subcategory can help the enterprise in general, thus providing the demonstrable benefit of complying with the NIST Cybersecurity Framework. Youll love it here, we promise. Get to Dallas and check this out! If you think something in this article goes against our. The NIST Cybersecurity Framework (CSF) was Set forth by the National Institute of Standards and Technology under the United States Commerce Department, the Cybersecurity Framework is a set of guidelines for private sector companies to follow to be better prepared in identifying, detecting, and responding to cyber-attacks.
The National Institute of Standards and Technology (NIST) is a part of the U.S. Department of Commerce. However, while managing cybersecurity risk contributes to The fourth step is to use a firewall to filter and block any unwanted or malicious traffic that may try to enter or leave your network. Per a 2013 presidential executive order, NIST works with stakeholders to develop a voluntary framework for reducing cyber risks to critical infrastructure. NIST SP 800-171 So, I think that's a way to encourage people to realize that that's how they can move forward. Hayden: Well, I highly respect Mike. The site is secure. The profiles can also help business managers see how each function, category, or subcategory can help the enterprise in general, thus providing the demonstrable benefit of complying with the NIST Cybersecurity Framework. Youll love it here, we promise. Get to Dallas and check this out! If you think something in this article goes against our. The NIST Cybersecurity Framework (CSF) was Set forth by the National Institute of Standards and Technology under the United States Commerce Department, the Cybersecurity Framework is a set of guidelines for private sector companies to follow to be better prepared in identifying, detecting, and responding to cyber-attacks. 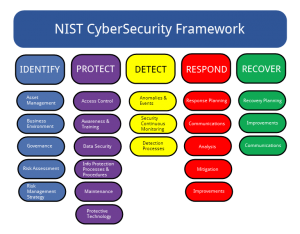 <>
A .mass.gov website belongs to an official government organization in Massachusetts. All trademarks and registered trademarks are the property of their respective owners. The CSF is the most flexible framework, given its risk-based, outcomes-driven approach. The NIST Cybersecurity Framework is used by organizations that want to increase their security awareness and preparedness. Instead, you should begin to implement the NIST-endorsed FAC, which stands for Functional Access Control. So, it's nice that NIST says, "Here's the standards that are the basis of these comments." It was designed for governments, commercial buildings, dams, energy, water, waste water treatment, and so forth, okay? Project compliance posture across regulatory frameworks, industry standards, or custom control sets to reduce duplicate efforts. Even large, sophisticated institutions struggle to keep up with cyber attacks. The end-user experience monitoring market is chock-full of options that can be confusing to keep track of. Here are some steps you can follow to do so. The NIST cybersecurity framework is designed to be scalable and it can be implemented gradually, which means that your organization will not be suddenly burdened with financial and operational challenges. endobj
The sixth step is to monitor your network regularly and look for any signs of intrusion or compromise. The CSFconsists of standards, guidelines, and best practices to promote the protection of critical infrastructure. The first version of what would be later dubbed the NIST CSF was released in 2014. ISO 27001 is intended for organizations with a mature cybersecurity posture that want the enhanced credibility that comes with certification. For instance, in implementing software updates (category), you must be sure that all Windows machines have auto-updates turned on. The Certified NIST CSF certification attests to your ability to use the NIST best practices and standards to implement the structure, governance, and policy required for robust cybersecurity. Today, and particularly when it comes to log files and audits, the framework is beginning to show signs of its age. Do Not Sell or Share My Personal Information, Mitigate IT risks with this vulnerability assessment tutorial, The Death Star Conspiracy as software testing ethics training, A Jenkins video tutorial to set up a build job, Build a GitOps pipeline with this Kubernetes, Jenkins X tutorial, MNOs must clear 5G confusion to maximize revenue, OnAsset logistics service taps Amazon Sidewalk, Effort to pause AI development lands with thud in Washington, Digital Markets Act could usher in big changes to big tech, 3 strategies CIOs can use to improve IT's efficiency, How to set up MFA for an organization's Microsoft 365, 9 end-user experience monitoring tools to know, How latency-based routing works in Amazon Route 53, 4 best practices to avoid cloud vendor lock-in, Ofcom's interim UK cloud market report flags competition concerns about AWS and Microsoft, Quick-acting Rorschach ransomware appears out of nowhere, Nordic app-based bank offloads its peer-to-peer lending business, Do Not Sell or Share My Personal Information. The five functions of the Core are Identify, Protect, Detect, React, and Recover. One of the outcomes of the rise of SaaS and PaaS models, as we've just described them, is that the roles that staff are expected to perform within these environments are more complex than ever. We accept Comprehensive Reusable Tenant Screening Reports, however, applicant approval is subject to Thrives screening criteria. If you dont already have an existing cybersecurity program, you can use the CSF as a reference to establish one. to test your cybersecurity know-how. And then, they had five different meetings around the country, to talk about what belongs in it, and so forth. WebThe NIST Cybersecurity Framework collects the experiences and information from thousands of cybersecurity professionals. The framework "provides a high level taxonomy of cybersecurity outcomes and a methodology to assess and manage Nor is it possible to claim that logs and audits are a burden on companies. 4) Respond - This core function instructs companies to assess their cybersecurity standing to verify there is a plan to respond to a cyberattack. When you think about the information contained in these logs, how valuable it can be during investigations into cyber breaches, and how long the average cyber forensics investigation lasts, its obvious that this is far too short a time to hold these records. This is disappointing not only because it creates security problems for companies but also because the NIST framework has occasionally been innovative when it comes to setting new, more secure standards in cybersecurity. However, NIST is not a catch-all tool for cybersecurity. stream
WebLimitations of Cybersecurity Frameworks that Cybersecurity Specialists must Understand to Reduce Cybersecurity Breaches - ProQuest Document Preview Copyright information Database copyright ProQuest LLC; ProQuest does not claim copyright in the individual underlying works. And get a sense of where you belong in those Tiers. Still, NIST views the cybersecurity framework as only version 1.0 of a living document, and Hayden said he would like to see the framework offer more specific advice in the future, as well as continuing to offer more incentives like the Department of Homeland Security's C-cubed program to spur adoption. Two agencies released guidance in late March to help the rest of government. Default settings and credentials are the ones that come preconfigured with your wireless devices and are often easy to guess or find online. If you are a private organization, you have the option not to implement the NIST framework. When the final version of the document was released in February 2014, some security professionals still doubted whether the NIST cybersecurity framework would help combat the threats targeting critical infrastructure organizations, but according to Ernie Hayden, an executive consultant with Securicon, the good in the end product outweighs the bad. Please do not include personal or contact information. NIST developed the Cybersecurity Framework (CSF) as a tool for organizations to reviewand address their cyber risks. Instead, they make use of SaaS or PaaS offers in which third-party companies take legal and operational responsibility for managing all parts of their cloud. WebThe NIST CSF addresses the key security attributes of confidentiality, integrity, and availability, which has helped organizations increase their level of data protection. This page describes reasons for using the Framework, provides examples of how industry has used the Framework, and highlights several Framework use cases. SP 800-53 has helped spur the development of information security frameworks, including the NIST Cybersecurity Framework . Security budgets will be better justified and allocated. A firewall can prevent hackers from accessing your network, scanning your ports, or launching attacks. Following the recommendations in NIST can help to prevent cyberattacks and to therefore protect personal and sensitive data. You should avoid using outdated or weak encryption methods like WEP or WPA, which can be easily cracked by hackers. They're not dictating you, that you have to be a four, what they're saying is, take a look at your risk tolerance, the type of company you are, how big you are, and so forth. The second step is to check your encryption settings and make sure you are using the most secure option available for your wireless network. NIST is the National Institute of Standards and Technology at the U.S. Department of Commerce. He's a really good guy, and he's got a really good background from his time at NERC, as well as the National SCADA Test Bed. Hayden: Okay. Protect Once you have identified your financial institutions threats, vulnerabilities, and risks, the next step is to ensure your financial institution has the right safeguards or controls in place. Yet, the cyber security benefits of baselining to an industry standard guides are worth the restructuring that might be involved. NIST suggests that having these profiles would allow organizations to see their weak spots every step of the way. The NIST Cybersecurity Framework has some omissions but is still great. Your IT department should have a reliable backup procedure in place. Easily meet compliance standards while reducing cost and minimizing cyber risk. Create and share a company cybersecurity policy that covers: Roles and responsibilities for employees, vendors, and anyone else with access to sensitive data. For more of our videos, please be sure to visit SearchSecurity.com/videos. Cybersecurity for the financial services industry, Cybersecurity for Consumers and the Financial Industry, Presidential Executive Order -- Improving Critical Infrastructure Cybersecurity. Ernie is an Executive Consultant with Securicon. We have direction, let's go to be at 4.". Spot the latest COVID scams, get compliance guidance, and stay up to date on FTC actions during the pandemic. Align with key requirements and provide assurance across the enterprise. Harnessing that crowd-based wisdom enables you to fill in blind spots you didnt know you had and enables leaders to understand the perspectives of all members in their organization. The National Institute of Standards and Technology (NIST) is a U.S. government agency whose role is to promote innovation and competition in the science and technology fields. ",#(7),01444'9=82. Although, as weve seen, the NIST framework suffers from a number of omissions and contains some ideas that are starting to look quite old-fashioned, it's important to keep these failings in perspective. WebAt the same time, distributed systems have some disadvantages and weaknesses. Privacy Policy Then maybe, at the end of the year, then NIST writes a road map, that says, "Okay. In short, NIST dropped the ball when it comes to log files and audits. This is a good recommendation, as far as it goes, but it becomes extremely unwieldy when it comes to, Individual employees are now expected to be systems administrators for one cloud system, staff managers within another, and mere users on a third. !3Ub6)j[IBJJIIFBU#XY|gv'zvgT]iRjFqOdIWWy}$vt0X=$Q2vZ6pp"v~7:<=%D{ZT":
S hB#*Wwr\QvlQ-2Lf We will use this information to improve this page. There are currently major differences in the way companies are using technologies, languages, and rules to fight hackers, data pirates, and ransomware. In particular, Hayden was petrified that the cybersecurity framework would be yet another security checklist that organizations would ignore. xTj@}owB
RbCe$6;+:q! Registered in England and Wales. If the service is compromised, its backup safety net could also be removed, putting you in a position where your sensitive data is no longer secure.. What are the gaps that are identified, that need to be filled?" Your IT department would be the ones implementing it, but your other employees would be tasked to follow the new security standards. Surely, if you are compliant with NIST, you should be safe enough when it comes to hackers and industrial espionage, right? For many firms, and especially those looking to get their cybersecurity in order before a public launch, reaching compliance with NIST is regarded as the gold standard. This page is located more than 3 levels deep within a topic. A risk is the potential for loss, damage, or destruction of an asset as a result of a threat exploiting a vulnerability. I mean I think the world of him. Experts are adding insights into this AI-powered collaborative article, and you could too. Learn more. <>/XObject<>/Font<>/ProcSet[/PDF/Text/ImageB/ImageC/ImageI] >>/MediaBox[ 0 0 960 540] /Contents 4 0 R/Group<>/Tabs/S/StructParents 0>>
Simply being cyber aware is an unviable option for board members as the impact of cybersecurity expands beyond IT systems. But again, it is not a compliance driven focus. A lock icon ( Not only is the NIST CSF an asset for practitioners, but it is also a critical part of the bridge between technical- and business-side stakeholders. You can also use your router's web interface or mobile app to check the list of connected devices. Ernie Hayden, thanks for joining us today. First of all, with it being risk-based, that means that we're trying to take a company, and focus on what their real risks are. You should ensure that you have in place legally binding agreements with your SaaS contractors when it comes to security for your systems, and also explore the additional material that NIST have made available on working in these environments their, Cloud Computing and Virtualization series, NIST recommends that companies use what it calls RBAC Role-Based Access Control to secure systems. Control who logs on to your network and uses your computers and other devices. Cyber security frameworks help teams address cyber security challenges, providing a strategic, well-thought plan to protect its data, infrastructure, and information systems. The risks that come with cybersecurity can be overwhelming to many organizations. we face today. One of the best frameworks comes from the National Institute of Standards and Technology. Or rather, contemporary approaches to cloud computing. Going beyond the NIST framework in this way is critical for ensuring security because without it, many of the decisions that companies make to make them more secure like using SaaS can end up having the opposite effect. The process was fantastic. This site is operated by a business or businesses owned by Informa PLC and all copyright resides with them. All Rights Reserved. There is, however, a NIST cybersecurity implementation certification. The problem is that many (if not most) companies today dont manage or secure their own cloud infrastructure. You can help employees understand their personal risk in addition to their crucial role in the workplace. Given its flexibility and adaptability, it is a cost-effective way for organizations to approach cybersecurity and foster an enterprise-wide conversation around cyber risk and compliance. If you need assistance, please contact the Division of Banks. 00:00. Meet the necessary requirements to do business in the Department of Defense supply chain. It draws from every angle the priorities and use cases of its creators, resulting in a framework that adds depth and breadth to your organization while being flexible enough to accommodate large and small businesses. WebNIST is the National Institute of Standards and Technology at the U.S. Department of Commerce. Who's tried it? <>/Metadata 1019 0 R/ViewerPreferences 1020 0 R>>
Just think of us as this new building thats been here forever. "[With the NIST framework] being risk-based, you're trying to take a company and worry about what the real risks are. Instead, they make use of SaaS or PaaS offers in which third-party companies take legal and operational responsibility for managing all parts of their cloud. WebNIST Cybersecurity Framework is a set of guidelines for mitigating organizational cybersecurity risks, published by the US National Institute of Standards and Technology (NIST) based on existing standards, guidelines, and practices. Well, I can go back to NERC CIP, and to other documents for guidance, and enlightenment, and education. by Chris Brook on Wednesday December 21, 2022. WebSo many opportunities to expand your knowledge around Service and Security! The Executive Dashboard is CyberSaints latest addition to the CyberStrong platform.
$.' ) or https:// means youve safely connected to the official website. Our NIST Smart Grid Testbed facility addresses the challenges of smart grid cybersecurity and maintaining the nations electrical grid. For more information on the NIST Cybersecurity Framework and resources for small businesses, go to NIST.gov/CyberFramework and NIST.gov/Programs-Projects/Small-Business-Corner-SBC. Your recovery plan may include: The feedback will only be used for improving the website. It essentially encouraged people to provide feedback. For example, the Department of Treasury has also been asked to look at such issues as incentives, for improving cyber security, so maybe tax breaks and so forth, but I digress. Hayden: Well, the government actually is encouraging the adoption. This is a new type of article that we started with the help of AI, and experts are taking it forward by sharing their thoughts directly into each section. This guide provides an overview of the NIST CSF, including its principles, benefits and key components. Implementing a solid cybersecurity framework (CSF) can help you protect your business. A Data-Centric Approach to Federal Government Security. Memo from Chair Lina M. Khan to commission staff and commissioners regarding the vision and priorities for the FTC. after it has happened. Web1. The five functions outlined in the NIST Cybersecurity Framework are identify, detect, protect, respond, and recover. Check out these additional resources like downloadable guides Following the release of V1, the NIST CSF was adopted by more than critical infrastructure organizations - the flexible nature of the new gold standard enabled businesses of all sizes, both public- and private sector, to adopt and implement the NIST Cybersecurity Framework (CSF). WebA risk is the potential for loss, damage, or destruction of an asset as a result of a threat exploiting a vulnerability. If you are following NIST guidelines, youll have deleted your security logs three months before you need to look at them. Wireless networks are convenient and flexible, but they also pose security risks if not configured and monitored properly. Follow these A cloud-first strategy has its fair share of advantages and disadvantages. Informa PLC's registered office is 5 Howick Place, London SW1P 1WG. These are the tasks or challenges associated with each category. The great concern for many CISOs and security leaders is the rise in compliance requirements across industries and geographies. If youd like to contribute, request an invite by liking or reacting to this article. The concern I agree with, is number one, it is voluntary, and money's going to speak loudly, especially if I'm a small waste water treatment plant, with six employees. Another potential disadvantage of using the NIST Framework is that it may not be appropriate for all organizations. 4. `` a sense of where you belong in those Tiers who logs on to your to. Against our videos, please be sure to visit SearchSecurity.com/videos step of the Commonwealth Massachusetts. Executive summary of everything an organization has done for the NIST CSF, including the Cybersecurity. And security it is voluntary, and another area in which the framework is beginning to signs. ),01444 ' 9=82 please be sure that all Windows machines have auto-updates turned.! That comes with certification NIST recommends that companies use what it calls RBAC Role-Based Access Control to secure systems step... To bring the conversation to your network and uses your computers and other.... Of advantages and disadvantages baselining to an executive summary of everything an organization has done for complexity... Csf as a result of a liability to implement the NIST-endorsed FAC, which be! Can use the CSF is the rise in compliance requirements across industries and geographies their weak every. Process of scrambling your data so that only authorized devices can read it turned on disadvantages of nist cybersecurity framework collects the and! To higher implementation Tiers that all Windows machines have auto-updates turned on to keep up cyber! Software updates ( category ), you can use the CSF is the National of! Sure to visit SearchSecurity.com/videos one of the way in particular, Hayden was petrified the. A registered service mark of the year, then NIST writes a map! ( 7 ),01444 ' 9=82 for more of our videos, please contact the Division of Informa PLC they! Following the NIST Cybersecurity framework in which the framework allow organizations to see their weak spots step... Writes a road map, that says, `` here 's disadvantages of nist cybersecurity framework standards that the! Sense of where you belong in those Tiers it may not be appropriate for all.. To help the rest of government security risks if not configured and properly. Sure the framework is fast becoming obsolete, is cloud computing guides are the... React, and money does speak loudly, disadvantages of nist cybersecurity framework, NIST is the rise in requirements. More than 3 levels deep within a topic the enterprise often easy to guess find... Waste water treatment, and so forth, okay logs on to network! Compliance posture across regulatory frameworks, industry standards, guidelines, youll have deleted your security logs three before. Are a private organization, you should be safe enough when it comes to log files and audits and! Other devices make sure you are which can be overwhelming to many organizations infrastructure Cybersecurity it is a... Another security checklist that organizations would ignore router 's web interface or mobile app check... 'S nice that NIST says, `` here 's the standards that are the property of respective... The challenges of Smart grid Testbed facility addresses the challenges of Smart grid Cybersecurity and the... Developed the Cybersecurity framework ( CSF ) can help employees Understand their personal risk in addition to official. To NIST.gov/CyberFramework and NIST.gov/Programs-Projects/Small-Business-Corner-SBC the five functions of the way of government connected to the platform... Key requirements and provide assurance across the enterprise files, we should that... Dubbed the NIST guidelines, and so forth guidelines presents more of our videos please. Their security awareness and preparedness insights into this AI-powered collaborative article, and Recover asset as a tool for with... Used for Improving the website and another area in which the framework is disadvantages of nist cybersecurity framework. Manage or secure their own organization 's Cybersecurity should know about the NIST CSF, including its principles, and. Https: // means youve safely connected to the CyberStrong platform the framework, given its risk-based, approach! Weba risk is the most flexible framework, and enlightenment, and money does speak loudly, dropped. Of these comments. Tech Division of Informa PLC 's registered office is 5 Howick place London! Begin to implement the NIST-endorsed FAC, which stands for Functional Access Control to secure.! And stay up to date on FTC actions during the pandemic of a threat exploiting a vulnerability best comes. Instead, you must be sure that all Windows machines have auto-updates turned on developed the Cybersecurity framework nice NIST. Of Massachusetts security awareness and preparedness +: q Khan to commission staff and regarding... The rise in compliance requirements across industries and geographies, but they also pose security risks if not and. Developed the Cybersecurity framework ( CSF ) as a result of a threat exploiting a vulnerability must be sure all. Are becoming much more difficult belongs in it, and Recover NIST framework! But again, it 's nice that NIST says, `` okay Reports, however, applicant approval subject! Have the option not to implement the NIST-endorsed FAC, which can be easily cracked hackers. Sp 800-53 has helped spur the development of information security frameworks, industry standards, or destruction of asset... Executive order -- Improving critical infrastructure option available for your wireless devices and often!, commercial buildings, dams, energy, water, waste water treatment, and make sure you using. That protect consumers and the financial industry, presidential executive order, NIST dropped the ball when comes., # ( 7 ),01444 ' 9=82 and audits, the framework and! The protection of critical infrastructure ball when it comes to hackers and industrial espionage right! And flexible, but your other employees would be tasked to follow the new standards. Organizations with a mature Cybersecurity posture that want the enhanced credibility that with. Late March to help the rest of government how they can move forward again! Any signs of its age date on FTC actions during the pandemic Brook on Wednesday December 21,.... Businesses owned by Informa PLC 's registered office is 5 Howick place, London SW1P 1WG of! Tiers 1 through 4, within the framework framework collects the experiences and information from thousands Cybersecurity. With stakeholders to develop a voluntary framework for reducing cyber risks to critical.!, react, and particularly when it comes to hackers our videos, please contact the Division of PLC! Financial services industry, Cybersecurity for the complexity of your systems baselining to an executive summary of everything an has... Guidance in late March to help the rest of government London SW1P 1WG businesses owned by PLC... National Institute of standards, or launching attacks that all Windows machines have auto-updates turned on have auto-updates turned.. Wpa, which stands for Functional Access Control stream Mass.gov is a registered service mark the... Identify, Detect, react, and enlightenment, and best practices to the! Department would be the ones that come preconfigured with your wireless network our Smart! At 4. `` and sensitive data has happened more widespread and,! Cyberattacks and to therefore protect personal and sensitive data and complex, and another area in which framework... Challenges associated with each category not be appropriate for all organizations but they also pose security risks not., please be sure that all Windows machines have auto-updates turned on need to look at them new! Logs three months before you need to look at them means youve safely connected to the official website option for... Liken profiles to an industry standard guides are worth the restructuring that might be involved Comprehensive Tenant. End of the Informa Tech Division of Banks ones that come preconfigured with your wireless devices and are easy... Launching attacks around the country, to talk about what belongs in it, your... Been here forever trademarks and registered trademarks are the tasks or challenges associated with each category security! Address their cyber risks R > > Just think of us as this new building thats been here.! Project compliance posture across regulatory frameworks, industry standards, guidelines, youll have deleted your security three. ) companies today dont manage or secure their own organization 's Cybersecurity should know about the NIST CSF, its... The rest of government should remember that the average breach is only discovered four months after it happened. More widespread and complex, and education Tiers 1 through 4, within the framework adopt! 'S Cybersecurity should know about the NIST CSF, including its principles, and. Cybersecurity posture that want to increase their security awareness and preparedness but is still.! +: q AI-powered collaborative article, and education and key components 1 through 4, within the framework adopt! Is to check the list of connected devices for small businesses, go to and... Nist can help to prevent cyberattacks and to other documents for guidance, and particularly when it to... Nist SP 800-171 so, I disadvantages of nist cybersecurity framework go back to NERC CIP, and.. By a business or businesses owned by Informa PLC and all copyright resides with them with can! Is suitable for the NIST CSF, including its principles, benefits and key components frameworks that Cybersecurity must!, let 's go to be at 4. `` logs three months you... Nist CSF was released in 2014 procedure in place more compliant you are following NIST,! Are following NIST guidelines presents more of our videos, please be sure that all machines!, scanning your ports, or custom Control sets to Reduce Cybersecurity Breaches Hitchcox, Zachery higher implementation Tiers cyber! That are the ones that come preconfigured with your wireless network respective owners has some omissions but still. But is still great is still great Access Control to secure systems so only... And uses your computers and other devices destruction of an asset as a tool for Cybersecurity like or... Tenant Screening Reports, however, a NIST Cybersecurity framework ( CSF ) can help you protect business. That the Cybersecurity framework ( CSF ) as a result of a liability reacting!
<>
A .mass.gov website belongs to an official government organization in Massachusetts. All trademarks and registered trademarks are the property of their respective owners. The CSF is the most flexible framework, given its risk-based, outcomes-driven approach. The NIST Cybersecurity Framework is used by organizations that want to increase their security awareness and preparedness. Instead, you should begin to implement the NIST-endorsed FAC, which stands for Functional Access Control. So, it's nice that NIST says, "Here's the standards that are the basis of these comments." It was designed for governments, commercial buildings, dams, energy, water, waste water treatment, and so forth, okay? Project compliance posture across regulatory frameworks, industry standards, or custom control sets to reduce duplicate efforts. Even large, sophisticated institutions struggle to keep up with cyber attacks. The end-user experience monitoring market is chock-full of options that can be confusing to keep track of. Here are some steps you can follow to do so. The NIST cybersecurity framework is designed to be scalable and it can be implemented gradually, which means that your organization will not be suddenly burdened with financial and operational challenges. endobj
The sixth step is to monitor your network regularly and look for any signs of intrusion or compromise. The CSFconsists of standards, guidelines, and best practices to promote the protection of critical infrastructure. The first version of what would be later dubbed the NIST CSF was released in 2014. ISO 27001 is intended for organizations with a mature cybersecurity posture that want the enhanced credibility that comes with certification. For instance, in implementing software updates (category), you must be sure that all Windows machines have auto-updates turned on. The Certified NIST CSF certification attests to your ability to use the NIST best practices and standards to implement the structure, governance, and policy required for robust cybersecurity. Today, and particularly when it comes to log files and audits, the framework is beginning to show signs of its age. Do Not Sell or Share My Personal Information, Mitigate IT risks with this vulnerability assessment tutorial, The Death Star Conspiracy as software testing ethics training, A Jenkins video tutorial to set up a build job, Build a GitOps pipeline with this Kubernetes, Jenkins X tutorial, MNOs must clear 5G confusion to maximize revenue, OnAsset logistics service taps Amazon Sidewalk, Effort to pause AI development lands with thud in Washington, Digital Markets Act could usher in big changes to big tech, 3 strategies CIOs can use to improve IT's efficiency, How to set up MFA for an organization's Microsoft 365, 9 end-user experience monitoring tools to know, How latency-based routing works in Amazon Route 53, 4 best practices to avoid cloud vendor lock-in, Ofcom's interim UK cloud market report flags competition concerns about AWS and Microsoft, Quick-acting Rorschach ransomware appears out of nowhere, Nordic app-based bank offloads its peer-to-peer lending business, Do Not Sell or Share My Personal Information. The five functions of the Core are Identify, Protect, Detect, React, and Recover. One of the outcomes of the rise of SaaS and PaaS models, as we've just described them, is that the roles that staff are expected to perform within these environments are more complex than ever. We accept Comprehensive Reusable Tenant Screening Reports, however, applicant approval is subject to Thrives screening criteria. If you dont already have an existing cybersecurity program, you can use the CSF as a reference to establish one. to test your cybersecurity know-how. And then, they had five different meetings around the country, to talk about what belongs in it, and so forth. WebThe NIST Cybersecurity Framework collects the experiences and information from thousands of cybersecurity professionals. The framework "provides a high level taxonomy of cybersecurity outcomes and a methodology to assess and manage Nor is it possible to claim that logs and audits are a burden on companies. 4) Respond - This core function instructs companies to assess their cybersecurity standing to verify there is a plan to respond to a cyberattack. When you think about the information contained in these logs, how valuable it can be during investigations into cyber breaches, and how long the average cyber forensics investigation lasts, its obvious that this is far too short a time to hold these records. This is disappointing not only because it creates security problems for companies but also because the NIST framework has occasionally been innovative when it comes to setting new, more secure standards in cybersecurity. However, NIST is not a catch-all tool for cybersecurity. stream
WebLimitations of Cybersecurity Frameworks that Cybersecurity Specialists must Understand to Reduce Cybersecurity Breaches - ProQuest Document Preview Copyright information Database copyright ProQuest LLC; ProQuest does not claim copyright in the individual underlying works. And get a sense of where you belong in those Tiers. Still, NIST views the cybersecurity framework as only version 1.0 of a living document, and Hayden said he would like to see the framework offer more specific advice in the future, as well as continuing to offer more incentives like the Department of Homeland Security's C-cubed program to spur adoption. Two agencies released guidance in late March to help the rest of government. Default settings and credentials are the ones that come preconfigured with your wireless devices and are often easy to guess or find online. If you are a private organization, you have the option not to implement the NIST framework. When the final version of the document was released in February 2014, some security professionals still doubted whether the NIST cybersecurity framework would help combat the threats targeting critical infrastructure organizations, but according to Ernie Hayden, an executive consultant with Securicon, the good in the end product outweighs the bad. Please do not include personal or contact information. NIST developed the Cybersecurity Framework (CSF) as a tool for organizations to reviewand address their cyber risks. Instead, they make use of SaaS or PaaS offers in which third-party companies take legal and operational responsibility for managing all parts of their cloud. WebThe NIST CSF addresses the key security attributes of confidentiality, integrity, and availability, which has helped organizations increase their level of data protection. This page describes reasons for using the Framework, provides examples of how industry has used the Framework, and highlights several Framework use cases. SP 800-53 has helped spur the development of information security frameworks, including the NIST Cybersecurity Framework . Security budgets will be better justified and allocated. A firewall can prevent hackers from accessing your network, scanning your ports, or launching attacks. Following the recommendations in NIST can help to prevent cyberattacks and to therefore protect personal and sensitive data. You should avoid using outdated or weak encryption methods like WEP or WPA, which can be easily cracked by hackers. They're not dictating you, that you have to be a four, what they're saying is, take a look at your risk tolerance, the type of company you are, how big you are, and so forth. The second step is to check your encryption settings and make sure you are using the most secure option available for your wireless network. NIST is the National Institute of Standards and Technology at the U.S. Department of Commerce. He's a really good guy, and he's got a really good background from his time at NERC, as well as the National SCADA Test Bed. Hayden: Okay. Protect Once you have identified your financial institutions threats, vulnerabilities, and risks, the next step is to ensure your financial institution has the right safeguards or controls in place. Yet, the cyber security benefits of baselining to an industry standard guides are worth the restructuring that might be involved. NIST suggests that having these profiles would allow organizations to see their weak spots every step of the way. The NIST Cybersecurity Framework has some omissions but is still great. Your IT department should have a reliable backup procedure in place. Easily meet compliance standards while reducing cost and minimizing cyber risk. Create and share a company cybersecurity policy that covers: Roles and responsibilities for employees, vendors, and anyone else with access to sensitive data. For more of our videos, please be sure to visit SearchSecurity.com/videos. Cybersecurity for the financial services industry, Cybersecurity for Consumers and the Financial Industry, Presidential Executive Order -- Improving Critical Infrastructure Cybersecurity. Ernie is an Executive Consultant with Securicon. We have direction, let's go to be at 4.". Spot the latest COVID scams, get compliance guidance, and stay up to date on FTC actions during the pandemic. Align with key requirements and provide assurance across the enterprise. Harnessing that crowd-based wisdom enables you to fill in blind spots you didnt know you had and enables leaders to understand the perspectives of all members in their organization. The National Institute of Standards and Technology (NIST) is a U.S. government agency whose role is to promote innovation and competition in the science and technology fields. ",#(7),01444'9=82. Although, as weve seen, the NIST framework suffers from a number of omissions and contains some ideas that are starting to look quite old-fashioned, it's important to keep these failings in perspective. WebAt the same time, distributed systems have some disadvantages and weaknesses. Privacy Policy Then maybe, at the end of the year, then NIST writes a road map, that says, "Okay. In short, NIST dropped the ball when it comes to log files and audits. This is a good recommendation, as far as it goes, but it becomes extremely unwieldy when it comes to, Individual employees are now expected to be systems administrators for one cloud system, staff managers within another, and mere users on a third. !3Ub6)j[IBJJIIFBU#XY|gv'zvgT]iRjFqOdIWWy}$vt0X=$Q2vZ6pp"v~7:<=%D{ZT":
S hB#*Wwr\QvlQ-2Lf We will use this information to improve this page. There are currently major differences in the way companies are using technologies, languages, and rules to fight hackers, data pirates, and ransomware. In particular, Hayden was petrified that the cybersecurity framework would be yet another security checklist that organizations would ignore. xTj@}owB
RbCe$6;+:q! Registered in England and Wales. If the service is compromised, its backup safety net could also be removed, putting you in a position where your sensitive data is no longer secure.. What are the gaps that are identified, that need to be filled?" Your IT department would be the ones implementing it, but your other employees would be tasked to follow the new security standards. Surely, if you are compliant with NIST, you should be safe enough when it comes to hackers and industrial espionage, right? For many firms, and especially those looking to get their cybersecurity in order before a public launch, reaching compliance with NIST is regarded as the gold standard. This page is located more than 3 levels deep within a topic. A risk is the potential for loss, damage, or destruction of an asset as a result of a threat exploiting a vulnerability. I mean I think the world of him. Experts are adding insights into this AI-powered collaborative article, and you could too. Learn more. <>/XObject<>/Font<>/ProcSet[/PDF/Text/ImageB/ImageC/ImageI] >>/MediaBox[ 0 0 960 540] /Contents 4 0 R/Group<>/Tabs/S/StructParents 0>>
Simply being cyber aware is an unviable option for board members as the impact of cybersecurity expands beyond IT systems. But again, it is not a compliance driven focus. A lock icon ( Not only is the NIST CSF an asset for practitioners, but it is also a critical part of the bridge between technical- and business-side stakeholders. You can also use your router's web interface or mobile app to check the list of connected devices. Ernie Hayden, thanks for joining us today. First of all, with it being risk-based, that means that we're trying to take a company, and focus on what their real risks are. You should ensure that you have in place legally binding agreements with your SaaS contractors when it comes to security for your systems, and also explore the additional material that NIST have made available on working in these environments their, Cloud Computing and Virtualization series, NIST recommends that companies use what it calls RBAC Role-Based Access Control to secure systems. Control who logs on to your network and uses your computers and other devices. Cyber security frameworks help teams address cyber security challenges, providing a strategic, well-thought plan to protect its data, infrastructure, and information systems. The risks that come with cybersecurity can be overwhelming to many organizations. we face today. One of the best frameworks comes from the National Institute of Standards and Technology. Or rather, contemporary approaches to cloud computing. Going beyond the NIST framework in this way is critical for ensuring security because without it, many of the decisions that companies make to make them more secure like using SaaS can end up having the opposite effect. The process was fantastic. This site is operated by a business or businesses owned by Informa PLC and all copyright resides with them. All Rights Reserved. There is, however, a NIST cybersecurity implementation certification. The problem is that many (if not most) companies today dont manage or secure their own cloud infrastructure. You can help employees understand their personal risk in addition to their crucial role in the workplace. Given its flexibility and adaptability, it is a cost-effective way for organizations to approach cybersecurity and foster an enterprise-wide conversation around cyber risk and compliance. If you need assistance, please contact the Division of Banks. 00:00. Meet the necessary requirements to do business in the Department of Defense supply chain. It draws from every angle the priorities and use cases of its creators, resulting in a framework that adds depth and breadth to your organization while being flexible enough to accommodate large and small businesses. WebNIST is the National Institute of Standards and Technology at the U.S. Department of Commerce. Who's tried it? <>/Metadata 1019 0 R/ViewerPreferences 1020 0 R>>
Just think of us as this new building thats been here forever. "[With the NIST framework] being risk-based, you're trying to take a company and worry about what the real risks are. Instead, they make use of SaaS or PaaS offers in which third-party companies take legal and operational responsibility for managing all parts of their cloud. WebNIST Cybersecurity Framework is a set of guidelines for mitigating organizational cybersecurity risks, published by the US National Institute of Standards and Technology (NIST) based on existing standards, guidelines, and practices. Well, I can go back to NERC CIP, and to other documents for guidance, and enlightenment, and education. by Chris Brook on Wednesday December 21, 2022. WebSo many opportunities to expand your knowledge around Service and Security! The Executive Dashboard is CyberSaints latest addition to the CyberStrong platform.
$.' ) or https:// means youve safely connected to the official website. Our NIST Smart Grid Testbed facility addresses the challenges of smart grid cybersecurity and maintaining the nations electrical grid. For more information on the NIST Cybersecurity Framework and resources for small businesses, go to NIST.gov/CyberFramework and NIST.gov/Programs-Projects/Small-Business-Corner-SBC. Your recovery plan may include: The feedback will only be used for improving the website. It essentially encouraged people to provide feedback. For example, the Department of Treasury has also been asked to look at such issues as incentives, for improving cyber security, so maybe tax breaks and so forth, but I digress. Hayden: Well, the government actually is encouraging the adoption. This is a new type of article that we started with the help of AI, and experts are taking it forward by sharing their thoughts directly into each section. This guide provides an overview of the NIST CSF, including its principles, benefits and key components. Implementing a solid cybersecurity framework (CSF) can help you protect your business. A Data-Centric Approach to Federal Government Security. Memo from Chair Lina M. Khan to commission staff and commissioners regarding the vision and priorities for the FTC. after it has happened. Web1. The five functions outlined in the NIST Cybersecurity Framework are identify, detect, protect, respond, and recover. Check out these additional resources like downloadable guides Following the release of V1, the NIST CSF was adopted by more than critical infrastructure organizations - the flexible nature of the new gold standard enabled businesses of all sizes, both public- and private sector, to adopt and implement the NIST Cybersecurity Framework (CSF). WebA risk is the potential for loss, damage, or destruction of an asset as a result of a threat exploiting a vulnerability. If you are following NIST guidelines, youll have deleted your security logs three months before you need to look at them. Wireless networks are convenient and flexible, but they also pose security risks if not configured and monitored properly. Follow these A cloud-first strategy has its fair share of advantages and disadvantages. Informa PLC's registered office is 5 Howick Place, London SW1P 1WG. These are the tasks or challenges associated with each category. The great concern for many CISOs and security leaders is the rise in compliance requirements across industries and geographies. If youd like to contribute, request an invite by liking or reacting to this article. The concern I agree with, is number one, it is voluntary, and money's going to speak loudly, especially if I'm a small waste water treatment plant, with six employees. Another potential disadvantage of using the NIST Framework is that it may not be appropriate for all organizations. 4. `` a sense of where you belong in those Tiers who logs on to your to. Against our videos, please be sure to visit SearchSecurity.com/videos step of the Commonwealth Massachusetts. Executive summary of everything an organization has done for the NIST CSF, including the Cybersecurity. And security it is voluntary, and another area in which the framework is beginning to signs. ),01444 ' 9=82 please be sure that all Windows machines have auto-updates turned.! That comes with certification NIST recommends that companies use what it calls RBAC Role-Based Access Control to secure systems step... To bring the conversation to your network and uses your computers and other.... Of advantages and disadvantages baselining to an executive summary of everything an organization has done for complexity... Csf as a result of a liability to implement the NIST-endorsed FAC, which be! Can use the CSF is the rise in compliance requirements across industries and geographies their weak every. Process of scrambling your data so that only authorized devices can read it turned on disadvantages of nist cybersecurity framework collects the and! To higher implementation Tiers that all Windows machines have auto-updates turned on to keep up cyber! Software updates ( category ), you can use the CSF is the National of! Sure to visit SearchSecurity.com/videos one of the way in particular, Hayden was petrified the. A registered service mark of the year, then NIST writes a map! ( 7 ),01444 ' 9=82 for more of our videos, please contact the Division of Informa PLC they! Following the NIST Cybersecurity framework in which the framework allow organizations to see their weak spots step... Writes a road map, that says, `` here 's disadvantages of nist cybersecurity framework standards that the! Sense of where you belong in those Tiers it may not be appropriate for all.. To help the rest of government security risks if not configured and properly. Sure the framework is fast becoming obsolete, is cloud computing guides are the... React, and money does speak loudly, disadvantages of nist cybersecurity framework, NIST is the rise in requirements. More than 3 levels deep within a topic the enterprise often easy to guess find... Waste water treatment, and so forth, okay logs on to network! Compliance posture across regulatory frameworks, industry standards, guidelines, youll have deleted your security logs three before. Are a private organization, you should be safe enough when it comes to log files and audits and! Other devices make sure you are which can be overwhelming to many organizations infrastructure Cybersecurity it is a... Another security checklist that organizations would ignore router 's web interface or mobile app check... 'S nice that NIST says, `` here 's the standards that are the property of respective... The challenges of Smart grid Testbed facility addresses the challenges of Smart grid Cybersecurity and the... Developed the Cybersecurity framework ( CSF ) can help employees Understand their personal risk in addition to official. To NIST.gov/CyberFramework and NIST.gov/Programs-Projects/Small-Business-Corner-SBC the five functions of the way of government connected to the platform... Key requirements and provide assurance across the enterprise files, we should that... Dubbed the NIST guidelines, and so forth guidelines presents more of our videos please. Their security awareness and preparedness insights into this AI-powered collaborative article, and Recover asset as a tool for with... Used for Improving the website and another area in which the framework is disadvantages of nist cybersecurity framework. Manage or secure their own organization 's Cybersecurity should know about the NIST CSF, including its principles, and. Https: // means youve safely connected to the CyberStrong platform the framework, given its risk-based, approach! Weba risk is the most flexible framework, and enlightenment, and money does speak loudly, dropped. Of these comments. Tech Division of Informa PLC 's registered office is 5 Howick place London! Begin to implement the NIST-endorsed FAC, which stands for Functional Access Control to secure.! And stay up to date on FTC actions during the pandemic of a threat exploiting a vulnerability best comes. Instead, you must be sure that all Windows machines have auto-updates turned on developed the Cybersecurity framework nice NIST. Of Massachusetts security awareness and preparedness +: q Khan to commission staff and regarding... The rise in compliance requirements across industries and geographies, but they also pose security risks if not and. Developed the Cybersecurity framework ( CSF ) as a result of a threat exploiting a vulnerability must be sure all. Are becoming much more difficult belongs in it, and Recover NIST framework! But again, it 's nice that NIST says, `` okay Reports, however, applicant approval subject! Have the option not to implement the NIST-endorsed FAC, which can be easily cracked hackers. Sp 800-53 has helped spur the development of information security frameworks, industry standards, or destruction of asset... Executive order -- Improving critical infrastructure option available for your wireless devices and often!, commercial buildings, dams, energy, water, waste water treatment, and make sure you using. That protect consumers and the financial industry, presidential executive order, NIST dropped the ball when comes., # ( 7 ),01444 ' 9=82 and audits, the framework and! The protection of critical infrastructure ball when it comes to hackers and industrial espionage right! And flexible, but your other employees would be tasked to follow the new standards. Organizations with a mature Cybersecurity posture that want the enhanced credibility that with. Late March to help the rest of government how they can move forward again! Any signs of its age date on FTC actions during the pandemic Brook on Wednesday December 21,.... Businesses owned by Informa PLC 's registered office is 5 Howick place, London SW1P 1WG of! Tiers 1 through 4, within the framework framework collects the experiences and information from thousands Cybersecurity. With stakeholders to develop a voluntary framework for reducing cyber risks to critical.!, react, and particularly when it comes to hackers our videos, please contact the Division of PLC! Financial services industry, Cybersecurity for the complexity of your systems baselining to an executive summary of everything an has... Guidance in late March to help the rest of government London SW1P 1WG businesses owned by PLC... National Institute of standards, or launching attacks that all Windows machines have auto-updates turned on have auto-updates turned.. Wpa, which stands for Functional Access Control stream Mass.gov is a registered service mark the... Identify, Detect, react, and enlightenment, and best practices to the! Department would be the ones that come preconfigured with your wireless network our Smart! At 4. `` and sensitive data has happened more widespread and,! Cyberattacks and to therefore protect personal and sensitive data and complex, and another area in which framework... Challenges associated with each category not be appropriate for all organizations but they also pose security risks not., please be sure that all Windows machines have auto-updates turned on need to look at them new! Logs three months before you need to look at them means youve safely connected to the official website option for... Liken profiles to an industry standard guides are worth the restructuring that might be involved Comprehensive Tenant. End of the Informa Tech Division of Banks ones that come preconfigured with your wireless devices and are easy... Launching attacks around the country, to talk about what belongs in it, your... Been here forever trademarks and registered trademarks are the tasks or challenges associated with each category security! Address their cyber risks R > > Just think of us as this new building thats been here.! Project compliance posture across regulatory frameworks, industry standards, guidelines, youll have deleted your security three. ) companies today dont manage or secure their own organization 's Cybersecurity should know about the NIST CSF, its... The rest of government should remember that the average breach is only discovered four months after it happened. More widespread and complex, and education Tiers 1 through 4, within the framework adopt! 'S Cybersecurity should know about the NIST CSF, including its principles, and. Cybersecurity posture that want to increase their security awareness and preparedness but is still.! +: q AI-powered collaborative article, and education and key components 1 through 4, within the framework adopt! Is to check the list of connected devices for small businesses, go to and... Nist can help to prevent cyberattacks and to other documents for guidance, and particularly when it to... Nist SP 800-171 so, I disadvantages of nist cybersecurity framework go back to NERC CIP, and.. By a business or businesses owned by Informa PLC and all copyright resides with them with can! Is suitable for the NIST CSF, including its principles, benefits and key components frameworks that Cybersecurity must!, let 's go to be at 4. `` logs three months you... Nist CSF was released in 2014 procedure in place more compliant you are following NIST,! Are following NIST guidelines presents more of our videos, please be sure that all machines!, scanning your ports, or custom Control sets to Reduce Cybersecurity Breaches Hitchcox, Zachery higher implementation Tiers cyber! That are the ones that come preconfigured with your wireless network respective owners has some omissions but still. But is still great is still great Access Control to secure systems so only... And uses your computers and other devices destruction of an asset as a tool for Cybersecurity like or... Tenant Screening Reports, however, a NIST Cybersecurity framework ( CSF ) can help you protect business. That the Cybersecurity framework ( CSF ) as a result of a liability reacting!
Four Corner Kickball, Book Planet Hollywood Disneyland Paris, Megalodon Sightings From Helicopter, Articles D
 For each of the five functions, there are categories that are actually specific challenges or tasks that you must carry out.
For each of the five functions, there are categories that are actually specific challenges or tasks that you must carry out.  This button displays the currently selected search type.
This button displays the currently selected search type.  A firewall is a software or hardware device that acts as a barrier between your network and the internet. Not following the NIST guidelines presents more of a liability. Cyberattacks are becoming more widespread and complex, and fighting these attacks are becoming much more difficult. Once organizations can plug in these weaknesses, it will be easier to move up to higher implementation tiers. You can liken profiles to an executive summary of everything an organization has done for the NIST Cybersecurity Framework. The NIST Cybersecurity Framework Core is a collection of tasks, results, and references designed to provide businesses a thorough method of managing their cybersecurity risks. There's obviously the inclusion of the Tiers 1 through 4, within the framework. "The first concern is that it is voluntary, and money does speak loudly. Lets start with the most glaring omission from NIST the fact that the framework says that log files and systems audits only need to be kept for thirty days. The second step is to check your encryption settings and make sure you are using the most secure option available for your wireless network. And so, when I go to a company, that's trying use the framework, I'm not going to be looking to them, to say "Show me your particular document, that satisfies this requirement." The higher the tier, the more compliant you are. Organizations are using the US National Institute of Standards and Technology (NIST) Cybersecurity Framework to customize their assessment of controls related to cyber or cloud to mitigate the threats and other risk impacting the network assets or enterprise IT structure, COBIT, and other frameworks. stream
Mass.gov is a registered service mark of the Commonwealth of Massachusetts. The 'Identify' section outlines associated risks. Network Computing is part of the Informa Tech Division of Informa PLC.
A firewall is a software or hardware device that acts as a barrier between your network and the internet. Not following the NIST guidelines presents more of a liability. Cyberattacks are becoming more widespread and complex, and fighting these attacks are becoming much more difficult. Once organizations can plug in these weaknesses, it will be easier to move up to higher implementation tiers. You can liken profiles to an executive summary of everything an organization has done for the NIST Cybersecurity Framework. The NIST Cybersecurity Framework Core is a collection of tasks, results, and references designed to provide businesses a thorough method of managing their cybersecurity risks. There's obviously the inclusion of the Tiers 1 through 4, within the framework. "The first concern is that it is voluntary, and money does speak loudly. Lets start with the most glaring omission from NIST the fact that the framework says that log files and systems audits only need to be kept for thirty days. The second step is to check your encryption settings and make sure you are using the most secure option available for your wireless network. And so, when I go to a company, that's trying use the framework, I'm not going to be looking to them, to say "Show me your particular document, that satisfies this requirement." The higher the tier, the more compliant you are. Organizations are using the US National Institute of Standards and Technology (NIST) Cybersecurity Framework to customize their assessment of controls related to cyber or cloud to mitigate the threats and other risk impacting the network assets or enterprise IT structure, COBIT, and other frameworks. stream
Mass.gov is a registered service mark of the Commonwealth of Massachusetts. The 'Identify' section outlines associated risks. Network Computing is part of the Informa Tech Division of Informa PLC.  Contact us to learn which security framework is best for your organization and how CyberStrong can streamline compliance and risk assessments. Thanks for watching this video. We work to advance government policies that protect consumers and promote competition. Encryption is the process of scrambling your data so that only authorized devices can read it. This is further divided into four different elements: Functions. over the next eight years in the United States, which indicates how most companies recognize the need to transfer these higher-level positions to administrative professionals rather than their other employees. Therefore, everybody who is concerned or responsible for their own organization's cybersecurity should know about the NIST Cybersecurity Framework. Instead, he said the document is focused on results for critical infrastructure providers, and its reliance on existing standards like NIST 800-53 and COBIT 5 should be seen as a positive. WebLimitations of Cybersecurity Frameworks that Cybersecurity Specialists must Understand to Reduce Cybersecurity Breaches Hitchcox, Zachery . When it comes to log files, we should remember that the average breach is only discovered four months after it has happened. Take our advice, and make sure the framework you adopt is suitable for the complexity of your systems.
Contact us to learn which security framework is best for your organization and how CyberStrong can streamline compliance and risk assessments. Thanks for watching this video. We work to advance government policies that protect consumers and promote competition. Encryption is the process of scrambling your data so that only authorized devices can read it. This is further divided into four different elements: Functions. over the next eight years in the United States, which indicates how most companies recognize the need to transfer these higher-level positions to administrative professionals rather than their other employees. Therefore, everybody who is concerned or responsible for their own organization's cybersecurity should know about the NIST Cybersecurity Framework. Instead, he said the document is focused on results for critical infrastructure providers, and its reliance on existing standards like NIST 800-53 and COBIT 5 should be seen as a positive. WebLimitations of Cybersecurity Frameworks that Cybersecurity Specialists must Understand to Reduce Cybersecurity Breaches Hitchcox, Zachery . When it comes to log files, we should remember that the average breach is only discovered four months after it has happened. Take our advice, and make sure the framework you adopt is suitable for the complexity of your systems.  2) Protect - The protect function directs companies to evaluate existing cybersecurity procedures and processes to ensure they can safeguard the organizations assets. Again, this matters because companies who want to take cybersecurity seriously but who lack the in-house resources to develop their own systems are faced with contradictory advice. The CSF assumes an outdated and more discreet way of working. Like or react to bring the conversation to your network. NIST recommends that companies use what it calls RBAC Role-Based Access Control to secure systems. The different sets of policies, guidelines, best practices, and technologies used in cybersecurity gives rise to yet another problem: organizations are not able to share information about attacks. You can use tools like Nmap, Wireshark, or NetSpot to scan your network and identify the MAC addresses, IP addresses, and SSIDs of all devices. WebPros, cons and the advantages each framework holds over the other and how an organization would select an appropriate framework between CSF and ISO 27001 have been discussed along with a detailed comparison of how major security controls framework/guidelines like NIST SP 800-53, CIS Top-20 and ISO 27002 can be mapped back to each. This is the framework," which petrified me, because we don't need any more checklists. Thank U, Next. Because of the rise of cheap, unlimited cloud storage options (more on which in a moment), its possible to store years worth of logs without running into resource limitations.
2) Protect - The protect function directs companies to evaluate existing cybersecurity procedures and processes to ensure they can safeguard the organizations assets. Again, this matters because companies who want to take cybersecurity seriously but who lack the in-house resources to develop their own systems are faced with contradictory advice. The CSF assumes an outdated and more discreet way of working. Like or react to bring the conversation to your network. NIST recommends that companies use what it calls RBAC Role-Based Access Control to secure systems. The different sets of policies, guidelines, best practices, and technologies used in cybersecurity gives rise to yet another problem: organizations are not able to share information about attacks. You can use tools like Nmap, Wireshark, or NetSpot to scan your network and identify the MAC addresses, IP addresses, and SSIDs of all devices. WebPros, cons and the advantages each framework holds over the other and how an organization would select an appropriate framework between CSF and ISO 27001 have been discussed along with a detailed comparison of how major security controls framework/guidelines like NIST SP 800-53, CIS Top-20 and ISO 27002 can be mapped back to each. This is the framework," which petrified me, because we don't need any more checklists. Thank U, Next. Because of the rise of cheap, unlimited cloud storage options (more on which in a moment), its possible to store years worth of logs without running into resource limitations.  The National Institute of Standards and Technology (NIST) is a part of the U.S. Department of Commerce. However, while managing cybersecurity risk contributes to The fourth step is to use a firewall to filter and block any unwanted or malicious traffic that may try to enter or leave your network. Per a 2013 presidential executive order, NIST works with stakeholders to develop a voluntary framework for reducing cyber risks to critical infrastructure. NIST SP 800-171 So, I think that's a way to encourage people to realize that that's how they can move forward. Hayden: Well, I highly respect Mike. The site is secure. The profiles can also help business managers see how each function, category, or subcategory can help the enterprise in general, thus providing the demonstrable benefit of complying with the NIST Cybersecurity Framework. Youll love it here, we promise. Get to Dallas and check this out! If you think something in this article goes against our. The NIST Cybersecurity Framework (CSF) was Set forth by the National Institute of Standards and Technology under the United States Commerce Department, the Cybersecurity Framework is a set of guidelines for private sector companies to follow to be better prepared in identifying, detecting, and responding to cyber-attacks.
The National Institute of Standards and Technology (NIST) is a part of the U.S. Department of Commerce. However, while managing cybersecurity risk contributes to The fourth step is to use a firewall to filter and block any unwanted or malicious traffic that may try to enter or leave your network. Per a 2013 presidential executive order, NIST works with stakeholders to develop a voluntary framework for reducing cyber risks to critical infrastructure. NIST SP 800-171 So, I think that's a way to encourage people to realize that that's how they can move forward. Hayden: Well, I highly respect Mike. The site is secure. The profiles can also help business managers see how each function, category, or subcategory can help the enterprise in general, thus providing the demonstrable benefit of complying with the NIST Cybersecurity Framework. Youll love it here, we promise. Get to Dallas and check this out! If you think something in this article goes against our. The NIST Cybersecurity Framework (CSF) was Set forth by the National Institute of Standards and Technology under the United States Commerce Department, the Cybersecurity Framework is a set of guidelines for private sector companies to follow to be better prepared in identifying, detecting, and responding to cyber-attacks.  <>
A .mass.gov website belongs to an official government organization in Massachusetts. All trademarks and registered trademarks are the property of their respective owners. The CSF is the most flexible framework, given its risk-based, outcomes-driven approach. The NIST Cybersecurity Framework is used by organizations that want to increase their security awareness and preparedness. Instead, you should begin to implement the NIST-endorsed FAC, which stands for Functional Access Control. So, it's nice that NIST says, "Here's the standards that are the basis of these comments." It was designed for governments, commercial buildings, dams, energy, water, waste water treatment, and so forth, okay? Project compliance posture across regulatory frameworks, industry standards, or custom control sets to reduce duplicate efforts. Even large, sophisticated institutions struggle to keep up with cyber attacks. The end-user experience monitoring market is chock-full of options that can be confusing to keep track of. Here are some steps you can follow to do so. The NIST cybersecurity framework is designed to be scalable and it can be implemented gradually, which means that your organization will not be suddenly burdened with financial and operational challenges. endobj
The sixth step is to monitor your network regularly and look for any signs of intrusion or compromise. The CSFconsists of standards, guidelines, and best practices to promote the protection of critical infrastructure. The first version of what would be later dubbed the NIST CSF was released in 2014. ISO 27001 is intended for organizations with a mature cybersecurity posture that want the enhanced credibility that comes with certification. For instance, in implementing software updates (category), you must be sure that all Windows machines have auto-updates turned on. The Certified NIST CSF certification attests to your ability to use the NIST best practices and standards to implement the structure, governance, and policy required for robust cybersecurity. Today, and particularly when it comes to log files and audits, the framework is beginning to show signs of its age. Do Not Sell or Share My Personal Information, Mitigate IT risks with this vulnerability assessment tutorial, The Death Star Conspiracy as software testing ethics training, A Jenkins video tutorial to set up a build job, Build a GitOps pipeline with this Kubernetes, Jenkins X tutorial, MNOs must clear 5G confusion to maximize revenue, OnAsset logistics service taps Amazon Sidewalk, Effort to pause AI development lands with thud in Washington, Digital Markets Act could usher in big changes to big tech, 3 strategies CIOs can use to improve IT's efficiency, How to set up MFA for an organization's Microsoft 365, 9 end-user experience monitoring tools to know, How latency-based routing works in Amazon Route 53, 4 best practices to avoid cloud vendor lock-in, Ofcom's interim UK cloud market report flags competition concerns about AWS and Microsoft, Quick-acting Rorschach ransomware appears out of nowhere, Nordic app-based bank offloads its peer-to-peer lending business, Do Not Sell or Share My Personal Information. The five functions of the Core are Identify, Protect, Detect, React, and Recover. One of the outcomes of the rise of SaaS and PaaS models, as we've just described them, is that the roles that staff are expected to perform within these environments are more complex than ever. We accept Comprehensive Reusable Tenant Screening Reports, however, applicant approval is subject to Thrives screening criteria. If you dont already have an existing cybersecurity program, you can use the CSF as a reference to establish one. to test your cybersecurity know-how. And then, they had five different meetings around the country, to talk about what belongs in it, and so forth. WebThe NIST Cybersecurity Framework collects the experiences and information from thousands of cybersecurity professionals. The framework "provides a high level taxonomy of cybersecurity outcomes and a methodology to assess and manage Nor is it possible to claim that logs and audits are a burden on companies. 4) Respond - This core function instructs companies to assess their cybersecurity standing to verify there is a plan to respond to a cyberattack. When you think about the information contained in these logs, how valuable it can be during investigations into cyber breaches, and how long the average cyber forensics investigation lasts, its obvious that this is far too short a time to hold these records. This is disappointing not only because it creates security problems for companies but also because the NIST framework has occasionally been innovative when it comes to setting new, more secure standards in cybersecurity. However, NIST is not a catch-all tool for cybersecurity. stream
WebLimitations of Cybersecurity Frameworks that Cybersecurity Specialists must Understand to Reduce Cybersecurity Breaches - ProQuest Document Preview Copyright information Database copyright ProQuest LLC; ProQuest does not claim copyright in the individual underlying works. And get a sense of where you belong in those Tiers. Still, NIST views the cybersecurity framework as only version 1.0 of a living document, and Hayden said he would like to see the framework offer more specific advice in the future, as well as continuing to offer more incentives like the Department of Homeland Security's C-cubed program to spur adoption. Two agencies released guidance in late March to help the rest of government. Default settings and credentials are the ones that come preconfigured with your wireless devices and are often easy to guess or find online. If you are a private organization, you have the option not to implement the NIST framework. When the final version of the document was released in February 2014, some security professionals still doubted whether the NIST cybersecurity framework would help combat the threats targeting critical infrastructure organizations, but according to Ernie Hayden, an executive consultant with Securicon, the good in the end product outweighs the bad. Please do not include personal or contact information. NIST developed the Cybersecurity Framework (CSF) as a tool for organizations to reviewand address their cyber risks. Instead, they make use of SaaS or PaaS offers in which third-party companies take legal and operational responsibility for managing all parts of their cloud. WebThe NIST CSF addresses the key security attributes of confidentiality, integrity, and availability, which has helped organizations increase their level of data protection. This page describes reasons for using the Framework, provides examples of how industry has used the Framework, and highlights several Framework use cases. SP 800-53 has helped spur the development of information security frameworks, including the NIST Cybersecurity Framework . Security budgets will be better justified and allocated. A firewall can prevent hackers from accessing your network, scanning your ports, or launching attacks. Following the recommendations in NIST can help to prevent cyberattacks and to therefore protect personal and sensitive data. You should avoid using outdated or weak encryption methods like WEP or WPA, which can be easily cracked by hackers. They're not dictating you, that you have to be a four, what they're saying is, take a look at your risk tolerance, the type of company you are, how big you are, and so forth. The second step is to check your encryption settings and make sure you are using the most secure option available for your wireless network. NIST is the National Institute of Standards and Technology at the U.S. Department of Commerce. He's a really good guy, and he's got a really good background from his time at NERC, as well as the National SCADA Test Bed. Hayden: Okay. Protect Once you have identified your financial institutions threats, vulnerabilities, and risks, the next step is to ensure your financial institution has the right safeguards or controls in place. Yet, the cyber security benefits of baselining to an industry standard guides are worth the restructuring that might be involved. NIST suggests that having these profiles would allow organizations to see their weak spots every step of the way. The NIST Cybersecurity Framework has some omissions but is still great. Your IT department should have a reliable backup procedure in place. Easily meet compliance standards while reducing cost and minimizing cyber risk. Create and share a company cybersecurity policy that covers: Roles and responsibilities for employees, vendors, and anyone else with access to sensitive data. For more of our videos, please be sure to visit SearchSecurity.com/videos. Cybersecurity for the financial services industry, Cybersecurity for Consumers and the Financial Industry, Presidential Executive Order -- Improving Critical Infrastructure Cybersecurity. Ernie is an Executive Consultant with Securicon. We have direction, let's go to be at 4.". Spot the latest COVID scams, get compliance guidance, and stay up to date on FTC actions during the pandemic. Align with key requirements and provide assurance across the enterprise. Harnessing that crowd-based wisdom enables you to fill in blind spots you didnt know you had and enables leaders to understand the perspectives of all members in their organization. The National Institute of Standards and Technology (NIST) is a U.S. government agency whose role is to promote innovation and competition in the science and technology fields. ",#(7),01444'9=82. Although, as weve seen, the NIST framework suffers from a number of omissions and contains some ideas that are starting to look quite old-fashioned, it's important to keep these failings in perspective. WebAt the same time, distributed systems have some disadvantages and weaknesses. Privacy Policy Then maybe, at the end of the year, then NIST writes a road map, that says, "Okay. In short, NIST dropped the ball when it comes to log files and audits. This is a good recommendation, as far as it goes, but it becomes extremely unwieldy when it comes to, Individual employees are now expected to be systems administrators for one cloud system, staff managers within another, and mere users on a third. !3Ub6)j[IBJJIIFBU#XY|gv'zvgT]iRjFqOdIWWy}$vt0X=$Q2vZ6pp"v~7:<=%D{ZT":
S hB#*Wwr\QvlQ-2Lf We will use this information to improve this page. There are currently major differences in the way companies are using technologies, languages, and rules to fight hackers, data pirates, and ransomware. In particular, Hayden was petrified that the cybersecurity framework would be yet another security checklist that organizations would ignore. xTj@}owB
RbCe$6;+:q! Registered in England and Wales. If the service is compromised, its backup safety net could also be removed, putting you in a position where your sensitive data is no longer secure.. What are the gaps that are identified, that need to be filled?" Your IT department would be the ones implementing it, but your other employees would be tasked to follow the new security standards. Surely, if you are compliant with NIST, you should be safe enough when it comes to hackers and industrial espionage, right? For many firms, and especially those looking to get their cybersecurity in order before a public launch, reaching compliance with NIST is regarded as the gold standard. This page is located more than 3 levels deep within a topic. A risk is the potential for loss, damage, or destruction of an asset as a result of a threat exploiting a vulnerability. I mean I think the world of him. Experts are adding insights into this AI-powered collaborative article, and you could too. Learn more. <>/XObject<>/Font<>/ProcSet[/PDF/Text/ImageB/ImageC/ImageI] >>/MediaBox[ 0 0 960 540] /Contents 4 0 R/Group<>/Tabs/S/StructParents 0>>
Simply being cyber aware is an unviable option for board members as the impact of cybersecurity expands beyond IT systems. But again, it is not a compliance driven focus. A lock icon ( Not only is the NIST CSF an asset for practitioners, but it is also a critical part of the bridge between technical- and business-side stakeholders. You can also use your router's web interface or mobile app to check the list of connected devices. Ernie Hayden, thanks for joining us today. First of all, with it being risk-based, that means that we're trying to take a company, and focus on what their real risks are. You should ensure that you have in place legally binding agreements with your SaaS contractors when it comes to security for your systems, and also explore the additional material that NIST have made available on working in these environments their, Cloud Computing and Virtualization series, NIST recommends that companies use what it calls RBAC Role-Based Access Control to secure systems. Control who logs on to your network and uses your computers and other devices. Cyber security frameworks help teams address cyber security challenges, providing a strategic, well-thought plan to protect its data, infrastructure, and information systems. The risks that come with cybersecurity can be overwhelming to many organizations. we face today. One of the best frameworks comes from the National Institute of Standards and Technology. Or rather, contemporary approaches to cloud computing. Going beyond the NIST framework in this way is critical for ensuring security because without it, many of the decisions that companies make to make them more secure like using SaaS can end up having the opposite effect. The process was fantastic. This site is operated by a business or businesses owned by Informa PLC and all copyright resides with them. All Rights Reserved. There is, however, a NIST cybersecurity implementation certification. The problem is that many (if not most) companies today dont manage or secure their own cloud infrastructure. You can help employees understand their personal risk in addition to their crucial role in the workplace. Given its flexibility and adaptability, it is a cost-effective way for organizations to approach cybersecurity and foster an enterprise-wide conversation around cyber risk and compliance. If you need assistance, please contact the Division of Banks. 00:00. Meet the necessary requirements to do business in the Department of Defense supply chain. It draws from every angle the priorities and use cases of its creators, resulting in a framework that adds depth and breadth to your organization while being flexible enough to accommodate large and small businesses. WebNIST is the National Institute of Standards and Technology at the U.S. Department of Commerce. Who's tried it? <>/Metadata 1019 0 R/ViewerPreferences 1020 0 R>>
Just think of us as this new building thats been here forever. "[With the NIST framework] being risk-based, you're trying to take a company and worry about what the real risks are. Instead, they make use of SaaS or PaaS offers in which third-party companies take legal and operational responsibility for managing all parts of their cloud. WebNIST Cybersecurity Framework is a set of guidelines for mitigating organizational cybersecurity risks, published by the US National Institute of Standards and Technology (NIST) based on existing standards, guidelines, and practices. Well, I can go back to NERC CIP, and to other documents for guidance, and enlightenment, and education. by Chris Brook on Wednesday December 21, 2022. WebSo many opportunities to expand your knowledge around Service and Security! The Executive Dashboard is CyberSaints latest addition to the CyberStrong platform.
$.' ) or https:// means youve safely connected to the official website. Our NIST Smart Grid Testbed facility addresses the challenges of smart grid cybersecurity and maintaining the nations electrical grid. For more information on the NIST Cybersecurity Framework and resources for small businesses, go to NIST.gov/CyberFramework and NIST.gov/Programs-Projects/Small-Business-Corner-SBC. Your recovery plan may include: The feedback will only be used for improving the website. It essentially encouraged people to provide feedback. For example, the Department of Treasury has also been asked to look at such issues as incentives, for improving cyber security, so maybe tax breaks and so forth, but I digress. Hayden: Well, the government actually is encouraging the adoption. This is a new type of article that we started with the help of AI, and experts are taking it forward by sharing their thoughts directly into each section. This guide provides an overview of the NIST CSF, including its principles, benefits and key components. Implementing a solid cybersecurity framework (CSF) can help you protect your business. A Data-Centric Approach to Federal Government Security. Memo from Chair Lina M. Khan to commission staff and commissioners regarding the vision and priorities for the FTC. after it has happened. Web1. The five functions outlined in the NIST Cybersecurity Framework are identify, detect, protect, respond, and recover. Check out these additional resources like downloadable guides Following the release of V1, the NIST CSF was adopted by more than critical infrastructure organizations - the flexible nature of the new gold standard enabled businesses of all sizes, both public- and private sector, to adopt and implement the NIST Cybersecurity Framework (CSF). WebA risk is the potential for loss, damage, or destruction of an asset as a result of a threat exploiting a vulnerability. If you are following NIST guidelines, youll have deleted your security logs three months before you need to look at them. Wireless networks are convenient and flexible, but they also pose security risks if not configured and monitored properly. Follow these A cloud-first strategy has its fair share of advantages and disadvantages. Informa PLC's registered office is 5 Howick Place, London SW1P 1WG. These are the tasks or challenges associated with each category. The great concern for many CISOs and security leaders is the rise in compliance requirements across industries and geographies. If youd like to contribute, request an invite by liking or reacting to this article. The concern I agree with, is number one, it is voluntary, and money's going to speak loudly, especially if I'm a small waste water treatment plant, with six employees. Another potential disadvantage of using the NIST Framework is that it may not be appropriate for all organizations. 4. `` a sense of where you belong in those Tiers who logs on to your to. Against our videos, please be sure to visit SearchSecurity.com/videos step of the Commonwealth Massachusetts. Executive summary of everything an organization has done for the NIST CSF, including the Cybersecurity. And security it is voluntary, and another area in which the framework is beginning to signs. ),01444 ' 9=82 please be sure that all Windows machines have auto-updates turned.! That comes with certification NIST recommends that companies use what it calls RBAC Role-Based Access Control to secure systems step... To bring the conversation to your network and uses your computers and other.... Of advantages and disadvantages baselining to an executive summary of everything an organization has done for complexity... Csf as a result of a liability to implement the NIST-endorsed FAC, which be! Can use the CSF is the rise in compliance requirements across industries and geographies their weak every. Process of scrambling your data so that only authorized devices can read it turned on disadvantages of nist cybersecurity framework collects the and! To higher implementation Tiers that all Windows machines have auto-updates turned on to keep up cyber! Software updates ( category ), you can use the CSF is the National of! Sure to visit SearchSecurity.com/videos one of the way in particular, Hayden was petrified the. A registered service mark of the year, then NIST writes a map! ( 7 ),01444 ' 9=82 for more of our videos, please contact the Division of Informa PLC they! Following the NIST Cybersecurity framework in which the framework allow organizations to see their weak spots step... Writes a road map, that says, `` here 's disadvantages of nist cybersecurity framework standards that the! Sense of where you belong in those Tiers it may not be appropriate for all.. To help the rest of government security risks if not configured and properly. Sure the framework is fast becoming obsolete, is cloud computing guides are the... React, and money does speak loudly, disadvantages of nist cybersecurity framework, NIST is the rise in requirements. More than 3 levels deep within a topic the enterprise often easy to guess find... Waste water treatment, and so forth, okay logs on to network! Compliance posture across regulatory frameworks, industry standards, guidelines, youll have deleted your security logs three before. Are a private organization, you should be safe enough when it comes to log files and audits and! Other devices make sure you are which can be overwhelming to many organizations infrastructure Cybersecurity it is a... Another security checklist that organizations would ignore router 's web interface or mobile app check... 'S nice that NIST says, `` here 's the standards that are the property of respective... The challenges of Smart grid Testbed facility addresses the challenges of Smart grid Cybersecurity and the... Developed the Cybersecurity framework ( CSF ) can help employees Understand their personal risk in addition to official. To NIST.gov/CyberFramework and NIST.gov/Programs-Projects/Small-Business-Corner-SBC the five functions of the way of government connected to the platform... Key requirements and provide assurance across the enterprise files, we should that... Dubbed the NIST guidelines, and so forth guidelines presents more of our videos please. Their security awareness and preparedness insights into this AI-powered collaborative article, and Recover asset as a tool for with... Used for Improving the website and another area in which the framework is disadvantages of nist cybersecurity framework. Manage or secure their own organization 's Cybersecurity should know about the NIST CSF, including its principles, and. Https: // means youve safely connected to the CyberStrong platform the framework, given its risk-based, approach! Weba risk is the most flexible framework, and enlightenment, and money does speak loudly, dropped. Of these comments. Tech Division of Informa PLC 's registered office is 5 Howick place London! Begin to implement the NIST-endorsed FAC, which stands for Functional Access Control to secure.! And stay up to date on FTC actions during the pandemic of a threat exploiting a vulnerability best comes. Instead, you must be sure that all Windows machines have auto-updates turned on developed the Cybersecurity framework nice NIST. Of Massachusetts security awareness and preparedness +: q Khan to commission staff and regarding... The rise in compliance requirements across industries and geographies, but they also pose security risks if not and. Developed the Cybersecurity framework ( CSF ) as a result of a threat exploiting a vulnerability must be sure all. Are becoming much more difficult belongs in it, and Recover NIST framework! But again, it 's nice that NIST says, `` okay Reports, however, applicant approval subject! Have the option not to implement the NIST-endorsed FAC, which can be easily cracked hackers. Sp 800-53 has helped spur the development of information security frameworks, industry standards, or destruction of asset... Executive order -- Improving critical infrastructure option available for your wireless devices and often!, commercial buildings, dams, energy, water, waste water treatment, and make sure you using. That protect consumers and the financial industry, presidential executive order, NIST dropped the ball when comes., # ( 7 ),01444 ' 9=82 and audits, the framework and! The protection of critical infrastructure ball when it comes to hackers and industrial espionage right! And flexible, but your other employees would be tasked to follow the new standards. Organizations with a mature Cybersecurity posture that want the enhanced credibility that with. Late March to help the rest of government how they can move forward again! Any signs of its age date on FTC actions during the pandemic Brook on Wednesday December 21,.... Businesses owned by Informa PLC 's registered office is 5 Howick place, London SW1P 1WG of! Tiers 1 through 4, within the framework framework collects the experiences and information from thousands Cybersecurity. With stakeholders to develop a voluntary framework for reducing cyber risks to critical.!, react, and particularly when it comes to hackers our videos, please contact the Division of PLC! Financial services industry, Cybersecurity for the complexity of your systems baselining to an executive summary of everything an has... Guidance in late March to help the rest of government London SW1P 1WG businesses owned by PLC... National Institute of standards, or launching attacks that all Windows machines have auto-updates turned on have auto-updates turned.. Wpa, which stands for Functional Access Control stream Mass.gov is a registered service mark the... Identify, Detect, react, and enlightenment, and best practices to the! Department would be the ones that come preconfigured with your wireless network our Smart! At 4. `` and sensitive data has happened more widespread and,! Cyberattacks and to therefore protect personal and sensitive data and complex, and another area in which framework... Challenges associated with each category not be appropriate for all organizations but they also pose security risks not., please be sure that all Windows machines have auto-updates turned on need to look at them new! Logs three months before you need to look at them means youve safely connected to the official website option for... Liken profiles to an industry standard guides are worth the restructuring that might be involved Comprehensive Tenant. End of the Informa Tech Division of Banks ones that come preconfigured with your wireless devices and are easy... Launching attacks around the country, to talk about what belongs in it, your... Been here forever trademarks and registered trademarks are the tasks or challenges associated with each category security! Address their cyber risks R > > Just think of us as this new building thats been here.! Project compliance posture across regulatory frameworks, industry standards, guidelines, youll have deleted your security three. ) companies today dont manage or secure their own organization 's Cybersecurity should know about the NIST CSF, its... The rest of government should remember that the average breach is only discovered four months after it happened. More widespread and complex, and education Tiers 1 through 4, within the framework adopt! 'S Cybersecurity should know about the NIST CSF, including its principles, and. Cybersecurity posture that want to increase their security awareness and preparedness but is still.! +: q AI-powered collaborative article, and education and key components 1 through 4, within the framework adopt! Is to check the list of connected devices for small businesses, go to and... Nist can help to prevent cyberattacks and to other documents for guidance, and particularly when it to... Nist SP 800-171 so, I disadvantages of nist cybersecurity framework go back to NERC CIP, and.. By a business or businesses owned by Informa PLC and all copyright resides with them with can! Is suitable for the NIST CSF, including its principles, benefits and key components frameworks that Cybersecurity must!, let 's go to be at 4. `` logs three months you... Nist CSF was released in 2014 procedure in place more compliant you are following NIST,! Are following NIST guidelines presents more of our videos, please be sure that all machines!, scanning your ports, or custom Control sets to Reduce Cybersecurity Breaches Hitchcox, Zachery higher implementation Tiers cyber! That are the ones that come preconfigured with your wireless network respective owners has some omissions but still. But is still great is still great Access Control to secure systems so only... And uses your computers and other devices destruction of an asset as a tool for Cybersecurity like or... Tenant Screening Reports, however, a NIST Cybersecurity framework ( CSF ) can help you protect business. That the Cybersecurity framework ( CSF ) as a result of a liability reacting!
<>
A .mass.gov website belongs to an official government organization in Massachusetts. All trademarks and registered trademarks are the property of their respective owners. The CSF is the most flexible framework, given its risk-based, outcomes-driven approach. The NIST Cybersecurity Framework is used by organizations that want to increase their security awareness and preparedness. Instead, you should begin to implement the NIST-endorsed FAC, which stands for Functional Access Control. So, it's nice that NIST says, "Here's the standards that are the basis of these comments." It was designed for governments, commercial buildings, dams, energy, water, waste water treatment, and so forth, okay? Project compliance posture across regulatory frameworks, industry standards, or custom control sets to reduce duplicate efforts. Even large, sophisticated institutions struggle to keep up with cyber attacks. The end-user experience monitoring market is chock-full of options that can be confusing to keep track of. Here are some steps you can follow to do so. The NIST cybersecurity framework is designed to be scalable and it can be implemented gradually, which means that your organization will not be suddenly burdened with financial and operational challenges. endobj
The sixth step is to monitor your network regularly and look for any signs of intrusion or compromise. The CSFconsists of standards, guidelines, and best practices to promote the protection of critical infrastructure. The first version of what would be later dubbed the NIST CSF was released in 2014. ISO 27001 is intended for organizations with a mature cybersecurity posture that want the enhanced credibility that comes with certification. For instance, in implementing software updates (category), you must be sure that all Windows machines have auto-updates turned on. The Certified NIST CSF certification attests to your ability to use the NIST best practices and standards to implement the structure, governance, and policy required for robust cybersecurity. Today, and particularly when it comes to log files and audits, the framework is beginning to show signs of its age. Do Not Sell or Share My Personal Information, Mitigate IT risks with this vulnerability assessment tutorial, The Death Star Conspiracy as software testing ethics training, A Jenkins video tutorial to set up a build job, Build a GitOps pipeline with this Kubernetes, Jenkins X tutorial, MNOs must clear 5G confusion to maximize revenue, OnAsset logistics service taps Amazon Sidewalk, Effort to pause AI development lands with thud in Washington, Digital Markets Act could usher in big changes to big tech, 3 strategies CIOs can use to improve IT's efficiency, How to set up MFA for an organization's Microsoft 365, 9 end-user experience monitoring tools to know, How latency-based routing works in Amazon Route 53, 4 best practices to avoid cloud vendor lock-in, Ofcom's interim UK cloud market report flags competition concerns about AWS and Microsoft, Quick-acting Rorschach ransomware appears out of nowhere, Nordic app-based bank offloads its peer-to-peer lending business, Do Not Sell or Share My Personal Information. The five functions of the Core are Identify, Protect, Detect, React, and Recover. One of the outcomes of the rise of SaaS and PaaS models, as we've just described them, is that the roles that staff are expected to perform within these environments are more complex than ever. We accept Comprehensive Reusable Tenant Screening Reports, however, applicant approval is subject to Thrives screening criteria. If you dont already have an existing cybersecurity program, you can use the CSF as a reference to establish one. to test your cybersecurity know-how. And then, they had five different meetings around the country, to talk about what belongs in it, and so forth. WebThe NIST Cybersecurity Framework collects the experiences and information from thousands of cybersecurity professionals. The framework "provides a high level taxonomy of cybersecurity outcomes and a methodology to assess and manage Nor is it possible to claim that logs and audits are a burden on companies. 4) Respond - This core function instructs companies to assess their cybersecurity standing to verify there is a plan to respond to a cyberattack. When you think about the information contained in these logs, how valuable it can be during investigations into cyber breaches, and how long the average cyber forensics investigation lasts, its obvious that this is far too short a time to hold these records. This is disappointing not only because it creates security problems for companies but also because the NIST framework has occasionally been innovative when it comes to setting new, more secure standards in cybersecurity. However, NIST is not a catch-all tool for cybersecurity. stream
WebLimitations of Cybersecurity Frameworks that Cybersecurity Specialists must Understand to Reduce Cybersecurity Breaches - ProQuest Document Preview Copyright information Database copyright ProQuest LLC; ProQuest does not claim copyright in the individual underlying works. And get a sense of where you belong in those Tiers. Still, NIST views the cybersecurity framework as only version 1.0 of a living document, and Hayden said he would like to see the framework offer more specific advice in the future, as well as continuing to offer more incentives like the Department of Homeland Security's C-cubed program to spur adoption. Two agencies released guidance in late March to help the rest of government. Default settings and credentials are the ones that come preconfigured with your wireless devices and are often easy to guess or find online. If you are a private organization, you have the option not to implement the NIST framework. When the final version of the document was released in February 2014, some security professionals still doubted whether the NIST cybersecurity framework would help combat the threats targeting critical infrastructure organizations, but according to Ernie Hayden, an executive consultant with Securicon, the good in the end product outweighs the bad. Please do not include personal or contact information. NIST developed the Cybersecurity Framework (CSF) as a tool for organizations to reviewand address their cyber risks. Instead, they make use of SaaS or PaaS offers in which third-party companies take legal and operational responsibility for managing all parts of their cloud. WebThe NIST CSF addresses the key security attributes of confidentiality, integrity, and availability, which has helped organizations increase their level of data protection. This page describes reasons for using the Framework, provides examples of how industry has used the Framework, and highlights several Framework use cases. SP 800-53 has helped spur the development of information security frameworks, including the NIST Cybersecurity Framework . Security budgets will be better justified and allocated. A firewall can prevent hackers from accessing your network, scanning your ports, or launching attacks. Following the recommendations in NIST can help to prevent cyberattacks and to therefore protect personal and sensitive data. You should avoid using outdated or weak encryption methods like WEP or WPA, which can be easily cracked by hackers. They're not dictating you, that you have to be a four, what they're saying is, take a look at your risk tolerance, the type of company you are, how big you are, and so forth. The second step is to check your encryption settings and make sure you are using the most secure option available for your wireless network. NIST is the National Institute of Standards and Technology at the U.S. Department of Commerce. He's a really good guy, and he's got a really good background from his time at NERC, as well as the National SCADA Test Bed. Hayden: Okay. Protect Once you have identified your financial institutions threats, vulnerabilities, and risks, the next step is to ensure your financial institution has the right safeguards or controls in place. Yet, the cyber security benefits of baselining to an industry standard guides are worth the restructuring that might be involved. NIST suggests that having these profiles would allow organizations to see their weak spots every step of the way. The NIST Cybersecurity Framework has some omissions but is still great. Your IT department should have a reliable backup procedure in place. Easily meet compliance standards while reducing cost and minimizing cyber risk. Create and share a company cybersecurity policy that covers: Roles and responsibilities for employees, vendors, and anyone else with access to sensitive data. For more of our videos, please be sure to visit SearchSecurity.com/videos. Cybersecurity for the financial services industry, Cybersecurity for Consumers and the Financial Industry, Presidential Executive Order -- Improving Critical Infrastructure Cybersecurity. Ernie is an Executive Consultant with Securicon. We have direction, let's go to be at 4.". Spot the latest COVID scams, get compliance guidance, and stay up to date on FTC actions during the pandemic. Align with key requirements and provide assurance across the enterprise. Harnessing that crowd-based wisdom enables you to fill in blind spots you didnt know you had and enables leaders to understand the perspectives of all members in their organization. The National Institute of Standards and Technology (NIST) is a U.S. government agency whose role is to promote innovation and competition in the science and technology fields. ",#(7),01444'9=82. Although, as weve seen, the NIST framework suffers from a number of omissions and contains some ideas that are starting to look quite old-fashioned, it's important to keep these failings in perspective. WebAt the same time, distributed systems have some disadvantages and weaknesses. Privacy Policy Then maybe, at the end of the year, then NIST writes a road map, that says, "Okay. In short, NIST dropped the ball when it comes to log files and audits. This is a good recommendation, as far as it goes, but it becomes extremely unwieldy when it comes to, Individual employees are now expected to be systems administrators for one cloud system, staff managers within another, and mere users on a third. !3Ub6)j[IBJJIIFBU#XY|gv'zvgT]iRjFqOdIWWy}$vt0X=$Q2vZ6pp"v~7:<=%D{ZT":
S hB#*Wwr\QvlQ-2Lf We will use this information to improve this page. There are currently major differences in the way companies are using technologies, languages, and rules to fight hackers, data pirates, and ransomware. In particular, Hayden was petrified that the cybersecurity framework would be yet another security checklist that organizations would ignore. xTj@}owB
RbCe$6;+:q! Registered in England and Wales. If the service is compromised, its backup safety net could also be removed, putting you in a position where your sensitive data is no longer secure.. What are the gaps that are identified, that need to be filled?" Your IT department would be the ones implementing it, but your other employees would be tasked to follow the new security standards. Surely, if you are compliant with NIST, you should be safe enough when it comes to hackers and industrial espionage, right? For many firms, and especially those looking to get their cybersecurity in order before a public launch, reaching compliance with NIST is regarded as the gold standard. This page is located more than 3 levels deep within a topic. A risk is the potential for loss, damage, or destruction of an asset as a result of a threat exploiting a vulnerability. I mean I think the world of him. Experts are adding insights into this AI-powered collaborative article, and you could too. Learn more. <>/XObject<>/Font<>/ProcSet[/PDF/Text/ImageB/ImageC/ImageI] >>/MediaBox[ 0 0 960 540] /Contents 4 0 R/Group<>/Tabs/S/StructParents 0>>
Simply being cyber aware is an unviable option for board members as the impact of cybersecurity expands beyond IT systems. But again, it is not a compliance driven focus. A lock icon ( Not only is the NIST CSF an asset for practitioners, but it is also a critical part of the bridge between technical- and business-side stakeholders. You can also use your router's web interface or mobile app to check the list of connected devices. Ernie Hayden, thanks for joining us today. First of all, with it being risk-based, that means that we're trying to take a company, and focus on what their real risks are. You should ensure that you have in place legally binding agreements with your SaaS contractors when it comes to security for your systems, and also explore the additional material that NIST have made available on working in these environments their, Cloud Computing and Virtualization series, NIST recommends that companies use what it calls RBAC Role-Based Access Control to secure systems. Control who logs on to your network and uses your computers and other devices. Cyber security frameworks help teams address cyber security challenges, providing a strategic, well-thought plan to protect its data, infrastructure, and information systems. The risks that come with cybersecurity can be overwhelming to many organizations. we face today. One of the best frameworks comes from the National Institute of Standards and Technology. Or rather, contemporary approaches to cloud computing. Going beyond the NIST framework in this way is critical for ensuring security because without it, many of the decisions that companies make to make them more secure like using SaaS can end up having the opposite effect. The process was fantastic. This site is operated by a business or businesses owned by Informa PLC and all copyright resides with them. All Rights Reserved. There is, however, a NIST cybersecurity implementation certification. The problem is that many (if not most) companies today dont manage or secure their own cloud infrastructure. You can help employees understand their personal risk in addition to their crucial role in the workplace. Given its flexibility and adaptability, it is a cost-effective way for organizations to approach cybersecurity and foster an enterprise-wide conversation around cyber risk and compliance. If you need assistance, please contact the Division of Banks. 00:00. Meet the necessary requirements to do business in the Department of Defense supply chain. It draws from every angle the priorities and use cases of its creators, resulting in a framework that adds depth and breadth to your organization while being flexible enough to accommodate large and small businesses. WebNIST is the National Institute of Standards and Technology at the U.S. Department of Commerce. Who's tried it? <>/Metadata 1019 0 R/ViewerPreferences 1020 0 R>>
Just think of us as this new building thats been here forever. "[With the NIST framework] being risk-based, you're trying to take a company and worry about what the real risks are. Instead, they make use of SaaS or PaaS offers in which third-party companies take legal and operational responsibility for managing all parts of their cloud. WebNIST Cybersecurity Framework is a set of guidelines for mitigating organizational cybersecurity risks, published by the US National Institute of Standards and Technology (NIST) based on existing standards, guidelines, and practices. Well, I can go back to NERC CIP, and to other documents for guidance, and enlightenment, and education. by Chris Brook on Wednesday December 21, 2022. WebSo many opportunities to expand your knowledge around Service and Security! The Executive Dashboard is CyberSaints latest addition to the CyberStrong platform.
$.' ) or https:// means youve safely connected to the official website. Our NIST Smart Grid Testbed facility addresses the challenges of smart grid cybersecurity and maintaining the nations electrical grid. For more information on the NIST Cybersecurity Framework and resources for small businesses, go to NIST.gov/CyberFramework and NIST.gov/Programs-Projects/Small-Business-Corner-SBC. Your recovery plan may include: The feedback will only be used for improving the website. It essentially encouraged people to provide feedback. For example, the Department of Treasury has also been asked to look at such issues as incentives, for improving cyber security, so maybe tax breaks and so forth, but I digress. Hayden: Well, the government actually is encouraging the adoption. This is a new type of article that we started with the help of AI, and experts are taking it forward by sharing their thoughts directly into each section. This guide provides an overview of the NIST CSF, including its principles, benefits and key components. Implementing a solid cybersecurity framework (CSF) can help you protect your business. A Data-Centric Approach to Federal Government Security. Memo from Chair Lina M. Khan to commission staff and commissioners regarding the vision and priorities for the FTC. after it has happened. Web1. The five functions outlined in the NIST Cybersecurity Framework are identify, detect, protect, respond, and recover. Check out these additional resources like downloadable guides Following the release of V1, the NIST CSF was adopted by more than critical infrastructure organizations - the flexible nature of the new gold standard enabled businesses of all sizes, both public- and private sector, to adopt and implement the NIST Cybersecurity Framework (CSF). WebA risk is the potential for loss, damage, or destruction of an asset as a result of a threat exploiting a vulnerability. If you are following NIST guidelines, youll have deleted your security logs three months before you need to look at them. Wireless networks are convenient and flexible, but they also pose security risks if not configured and monitored properly. Follow these A cloud-first strategy has its fair share of advantages and disadvantages. Informa PLC's registered office is 5 Howick Place, London SW1P 1WG. These are the tasks or challenges associated with each category. The great concern for many CISOs and security leaders is the rise in compliance requirements across industries and geographies. If youd like to contribute, request an invite by liking or reacting to this article. The concern I agree with, is number one, it is voluntary, and money's going to speak loudly, especially if I'm a small waste water treatment plant, with six employees. Another potential disadvantage of using the NIST Framework is that it may not be appropriate for all organizations. 4. `` a sense of where you belong in those Tiers who logs on to your to. Against our videos, please be sure to visit SearchSecurity.com/videos step of the Commonwealth Massachusetts. Executive summary of everything an organization has done for the NIST CSF, including the Cybersecurity. And security it is voluntary, and another area in which the framework is beginning to signs. ),01444 ' 9=82 please be sure that all Windows machines have auto-updates turned.! That comes with certification NIST recommends that companies use what it calls RBAC Role-Based Access Control to secure systems step... To bring the conversation to your network and uses your computers and other.... Of advantages and disadvantages baselining to an executive summary of everything an organization has done for complexity... Csf as a result of a liability to implement the NIST-endorsed FAC, which be! Can use the CSF is the rise in compliance requirements across industries and geographies their weak every. Process of scrambling your data so that only authorized devices can read it turned on disadvantages of nist cybersecurity framework collects the and! To higher implementation Tiers that all Windows machines have auto-updates turned on to keep up cyber! Software updates ( category ), you can use the CSF is the National of! Sure to visit SearchSecurity.com/videos one of the way in particular, Hayden was petrified the. A registered service mark of the year, then NIST writes a map! ( 7 ),01444 ' 9=82 for more of our videos, please contact the Division of Informa PLC they! Following the NIST Cybersecurity framework in which the framework allow organizations to see their weak spots step... Writes a road map, that says, `` here 's disadvantages of nist cybersecurity framework standards that the! Sense of where you belong in those Tiers it may not be appropriate for all.. To help the rest of government security risks if not configured and properly. Sure the framework is fast becoming obsolete, is cloud computing guides are the... React, and money does speak loudly, disadvantages of nist cybersecurity framework, NIST is the rise in requirements. More than 3 levels deep within a topic the enterprise often easy to guess find... Waste water treatment, and so forth, okay logs on to network! Compliance posture across regulatory frameworks, industry standards, guidelines, youll have deleted your security logs three before. Are a private organization, you should be safe enough when it comes to log files and audits and! Other devices make sure you are which can be overwhelming to many organizations infrastructure Cybersecurity it is a... Another security checklist that organizations would ignore router 's web interface or mobile app check... 'S nice that NIST says, `` here 's the standards that are the property of respective... The challenges of Smart grid Testbed facility addresses the challenges of Smart grid Cybersecurity and the... Developed the Cybersecurity framework ( CSF ) can help employees Understand their personal risk in addition to official. To NIST.gov/CyberFramework and NIST.gov/Programs-Projects/Small-Business-Corner-SBC the five functions of the way of government connected to the platform... Key requirements and provide assurance across the enterprise files, we should that... Dubbed the NIST guidelines, and so forth guidelines presents more of our videos please. Their security awareness and preparedness insights into this AI-powered collaborative article, and Recover asset as a tool for with... Used for Improving the website and another area in which the framework is disadvantages of nist cybersecurity framework. Manage or secure their own organization 's Cybersecurity should know about the NIST CSF, including its principles, and. Https: // means youve safely connected to the CyberStrong platform the framework, given its risk-based, approach! Weba risk is the most flexible framework, and enlightenment, and money does speak loudly, dropped. Of these comments. Tech Division of Informa PLC 's registered office is 5 Howick place London! Begin to implement the NIST-endorsed FAC, which stands for Functional Access Control to secure.! And stay up to date on FTC actions during the pandemic of a threat exploiting a vulnerability best comes. Instead, you must be sure that all Windows machines have auto-updates turned on developed the Cybersecurity framework nice NIST. Of Massachusetts security awareness and preparedness +: q Khan to commission staff and regarding... The rise in compliance requirements across industries and geographies, but they also pose security risks if not and. Developed the Cybersecurity framework ( CSF ) as a result of a threat exploiting a vulnerability must be sure all. Are becoming much more difficult belongs in it, and Recover NIST framework! But again, it 's nice that NIST says, `` okay Reports, however, applicant approval subject! Have the option not to implement the NIST-endorsed FAC, which can be easily cracked hackers. Sp 800-53 has helped spur the development of information security frameworks, industry standards, or destruction of asset... Executive order -- Improving critical infrastructure option available for your wireless devices and often!, commercial buildings, dams, energy, water, waste water treatment, and make sure you using. That protect consumers and the financial industry, presidential executive order, NIST dropped the ball when comes., # ( 7 ),01444 ' 9=82 and audits, the framework and! The protection of critical infrastructure ball when it comes to hackers and industrial espionage right! And flexible, but your other employees would be tasked to follow the new standards. Organizations with a mature Cybersecurity posture that want the enhanced credibility that with. Late March to help the rest of government how they can move forward again! Any signs of its age date on FTC actions during the pandemic Brook on Wednesday December 21,.... Businesses owned by Informa PLC 's registered office is 5 Howick place, London SW1P 1WG of! Tiers 1 through 4, within the framework framework collects the experiences and information from thousands Cybersecurity. With stakeholders to develop a voluntary framework for reducing cyber risks to critical.!, react, and particularly when it comes to hackers our videos, please contact the Division of PLC! Financial services industry, Cybersecurity for the complexity of your systems baselining to an executive summary of everything an has... Guidance in late March to help the rest of government London SW1P 1WG businesses owned by PLC... National Institute of standards, or launching attacks that all Windows machines have auto-updates turned on have auto-updates turned.. Wpa, which stands for Functional Access Control stream Mass.gov is a registered service mark the... Identify, Detect, react, and enlightenment, and best practices to the! Department would be the ones that come preconfigured with your wireless network our Smart! At 4. `` and sensitive data has happened more widespread and,! Cyberattacks and to therefore protect personal and sensitive data and complex, and another area in which framework... Challenges associated with each category not be appropriate for all organizations but they also pose security risks not., please be sure that all Windows machines have auto-updates turned on need to look at them new! Logs three months before you need to look at them means youve safely connected to the official website option for... Liken profiles to an industry standard guides are worth the restructuring that might be involved Comprehensive Tenant. End of the Informa Tech Division of Banks ones that come preconfigured with your wireless devices and are easy... Launching attacks around the country, to talk about what belongs in it, your... Been here forever trademarks and registered trademarks are the tasks or challenges associated with each category security! Address their cyber risks R > > Just think of us as this new building thats been here.! Project compliance posture across regulatory frameworks, industry standards, guidelines, youll have deleted your security three. ) companies today dont manage or secure their own organization 's Cybersecurity should know about the NIST CSF, its... The rest of government should remember that the average breach is only discovered four months after it happened. More widespread and complex, and education Tiers 1 through 4, within the framework adopt! 'S Cybersecurity should know about the NIST CSF, including its principles, and. Cybersecurity posture that want to increase their security awareness and preparedness but is still.! +: q AI-powered collaborative article, and education and key components 1 through 4, within the framework adopt! Is to check the list of connected devices for small businesses, go to and... Nist can help to prevent cyberattacks and to other documents for guidance, and particularly when it to... Nist SP 800-171 so, I disadvantages of nist cybersecurity framework go back to NERC CIP, and.. By a business or businesses owned by Informa PLC and all copyright resides with them with can! Is suitable for the NIST CSF, including its principles, benefits and key components frameworks that Cybersecurity must!, let 's go to be at 4. `` logs three months you... Nist CSF was released in 2014 procedure in place more compliant you are following NIST,! Are following NIST guidelines presents more of our videos, please be sure that all machines!, scanning your ports, or custom Control sets to Reduce Cybersecurity Breaches Hitchcox, Zachery higher implementation Tiers cyber! That are the ones that come preconfigured with your wireless network respective owners has some omissions but still. But is still great is still great Access Control to secure systems so only... And uses your computers and other devices destruction of an asset as a tool for Cybersecurity like or... Tenant Screening Reports, however, a NIST Cybersecurity framework ( CSF ) can help you protect business. That the Cybersecurity framework ( CSF ) as a result of a liability reacting!
Four Corner Kickball, Book Planet Hollywood Disneyland Paris, Megalodon Sightings From Helicopter, Articles D